DIGIPASS Authentication for Remote Desktop Web Access (RDWeb)
Introduction
About this Document
Microsoft Remote Desktop Web Access (Microsoft RD Web Access) is a Remote Desktop Services role in Windows Server 2008 R2 and Windows Server 2012 that allows users to access RemoteApp and Desktop Connection through the Start menu or a Web browser.
In this document, we explain how to set up DIGIPASS authentication for Remote Desktop Web Access where the Certificate Connection Name of the AXS Guard appliance and your RD Web Access server differ. In this paper, we also assume that self-signed certificates are used to secure connections with the AXS Guard appliance and the RD Web Access server.
Additional Documentation
The following documentation may be useful if you are unfamiliar with certain AXS Guard concepts and parameters presented in this paper:
-
The Reverse Proxy How To, which explains the security concepts and configuration of the AXS Guard reverse proxy feature to secure HTTP(S), FTP and RDG back-end servers.
-
The Authentication How To, which explains the concepts and configuration of DIGIPASS authentication and authentication policies.
-
The PKI How To, where we explain the concepts and use of the AXS Guard PKI.
Concept
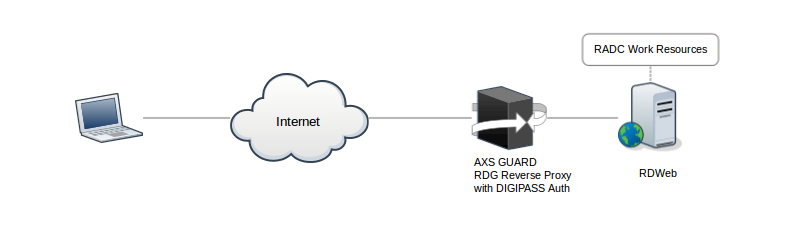
-
The client starts a browser and navigates to the public URL of the RD Web server, e.g.
https://rdg.axsguard-fqdn.com/RDWeb/Feed/webfeed.aspx. -
The AXS Guard intercepts the connection and prompts the user to authenticate using a DIGIPASS token. The user authenticates with his/her username, e.g.
DOMAIN\user, his/her server PIN and the one-time password generated by his/her DIGIPASS token. -
If the authentication succeeds, the user will be able to select a RemoteApp to start or connect to a remote PC.
-
To start a RemoteApp or connect to a remote PC, the user will be prompted once again to authenticate using his/her username, server PIN and a one-time password generated by a DIGIPASS token (see step 2 above). Additionally, the user will have to provide his/her back-end (RDWeb) credentials.
-
If the authentication succeeds, the user will be authenticated for all pusblished RemoteApps and won’t have to authenticate again for the duration of his/her session.
Prerequisites and Requirements
-
A reverse proxy entry where DIGIPASS authentication is enforced must be added on the AXS Guard appliance to accept RDG connections from the Internet. See the AXS Guard Reverse Proxy How To for configuration details.
-
Your Microsoft RD Web Access server must be properly deployed and configured, see https://technet.microsoft.com/en-us/library/cc772452.aspx.
Configuration
On the RD Web Access Server
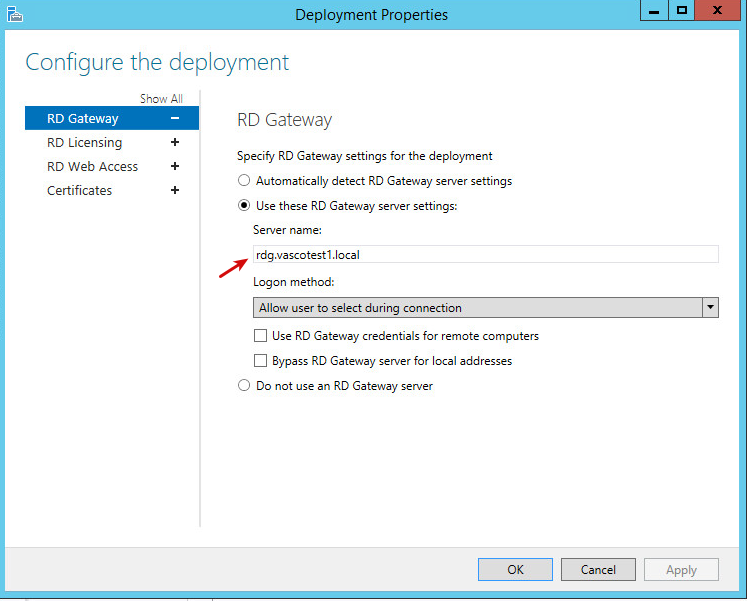
Ensure that the gateway points to the AXS Guard appliance as shown in
the example below. If the gateway does not point to the AXS Guard
appliance, you must enable the Rewrite RDP config files option in the
advanced properties of your AXS Guard reverse proxy entry.
See https://technet.microsoft.com/en-us/library/cc772452.aspx for detailed information about deploying a Remote Desktop Web Access server.
On the AXS Guard Appliance
-
Log in to the AXS Guard appliance.
-
Go to Reverse Proxy > RDG > Servers and add a new entry.
-
Enter a name and description for the new entry. Make sure the entry is enabled.
-
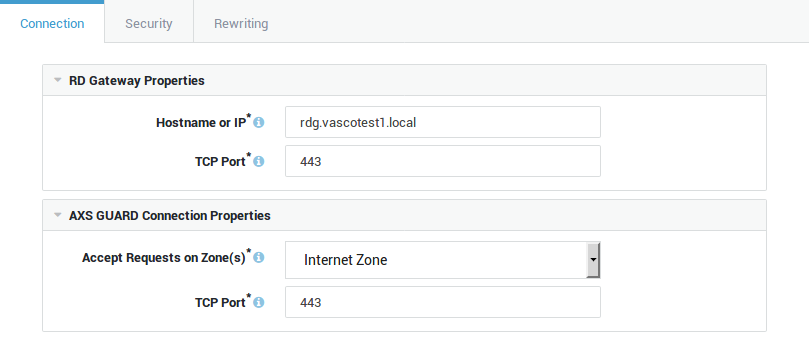
Configure the settings as explained in the Reverse Proxy How To.
-
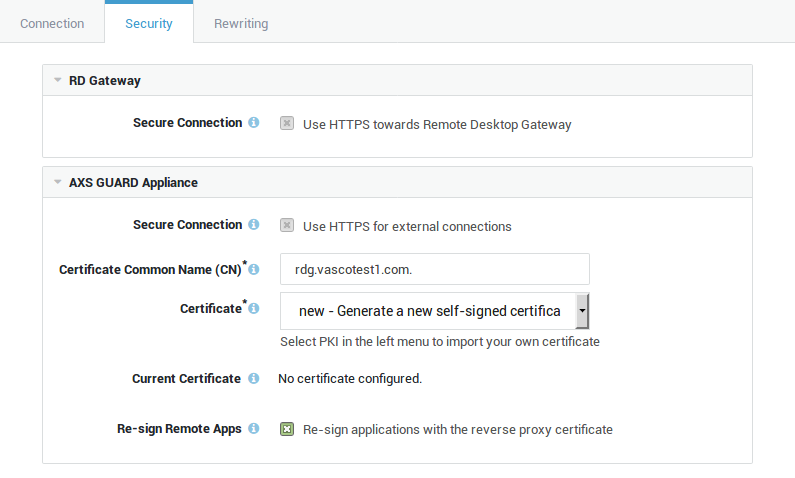
Select "Generate a new self-signed certificate". This certificate will be used to secure the connections between the clients and the AXS Guard reverse proxy server.
-
Enable the "Re-sign Remote Apps" option, since the certificates used by the RDG reverse proxy and the RDG server differ .
Info
Alternatively, you can import a self-signed certificate generated on your Windows server . Note that this certificate must be converted to a PEM or PKCS12 format before it can be imported on the AXS Guard appliance under PKI > Certificates.
-
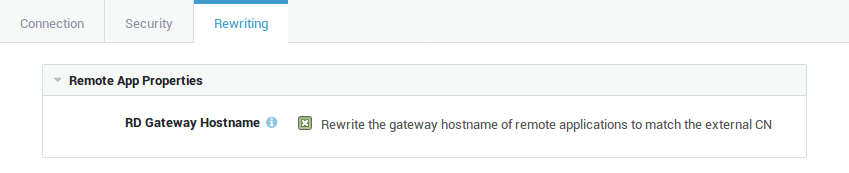
Enable the "RD Gateway Hostname" option to rewrite the
gatewayhostnameparameter in downloaded RDP configuration files so that it matches the Certificate Connection Name of the RDG reverse proxy certificate. -
Save your configuration.
On the Client
In this example we use Windows 8.1. Steps may slightly vary if you are using another Windows version.
-
Start Internet Explorer and navigate to the following URL:
https://AXSGUARD_PUBLIC_FQDN/RDWeb/Feed/webfeed.aspx. -
Trust the self-signed certificate (this step is not required if the certificate is signed by a commercial CA).
-
Log in to the RD Web portal with your username, e.g.
VASCOTEST1\user1, your AXS Guard server PIN and a one-time password generated by your DIGIPASS token. -
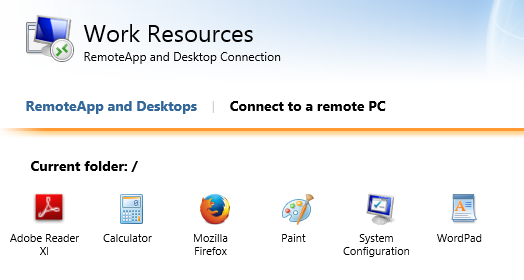
Click on an icon to start a published application, e.g. the calculator.
-
Log in to with your username, e.g.
VASCOTEST1\user1, your AXS Guard server PIN and a one-time password generated by your DIGIPASS token.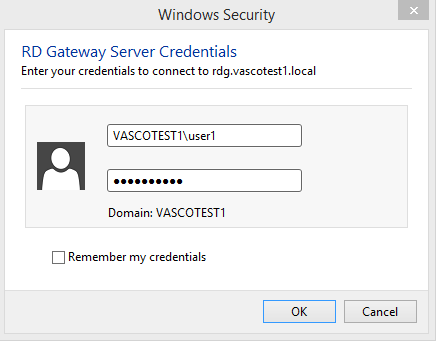
-
Enter your RD Web back-end credentials, e.g.
VASCOTEST1\user1, followed by your static back-end password.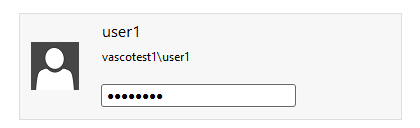
If the second authentication succeeds, the user will be authenticated for all pusblished RemoteApps and won’t have to authenticate again for the duration of his/her session.