Automated Proxy Detection
Introduction
About this Document
In this document we explain how to configure automatic proxy detection (WPAD) on the AXS Guard appliance. This document was last updated on 8 Dec 2020.
Before you start
-
Read the appropriate WPAD sections in the web access guide or consult the appliance’s context-sensitive help.
-
Configure the WPAD options on the AXS Guard appliance.
WPAD in a Nutshell
To use automatic proxy detection, you need to enable the Web Access feature on AXS Guard.
The client will attempt to resolve wpad.example.com where
example.com is the client’s configured domain. wpad.example.com
should resolve to the LAN IP address of the AXS Guard appliance.
The client then connects to the AXS Guard appliance and looks for the proxy information in the wpad.dat file. The hostname in the wpad.dat file must also be resolvable by the client.
The default location for this file is
http://wpad.yourdomain.com/wpad.dat. The file can be modified if
needed.
There are two ways the wpad.dat file can be be discovered by a client, i.e. via DHCP or via DNS. The configuration varies depending on whether or not you are using your own DNS or DHCP server or AXS Guard DHCP and DNS services.
Using AXS Guard DHCP and DNS Services
DHCP
-
Go to Network > DHCP > Address Pools
-
Select the appropriate pool for clients that will be using WPAD or create a new one.
-
Click on the DHCP Options tab.
-
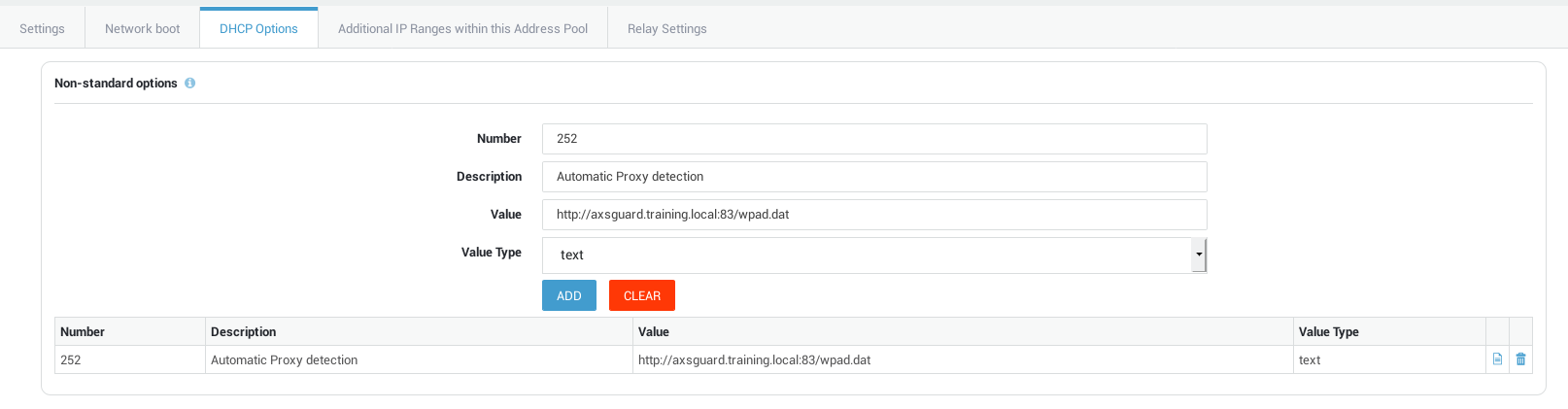
Enter and add the following non-standard options:
-
Number =
252 -
Description = Enter a text of your choice
-
Value =
http://AXSGUARD_FQDN:83/wpad.dat -
Value Type =
text
-
DNS
The appliance automatically creates a WPAD CNAME record
wpad.example.com. Clients which use the AXS Guard DNS server will be
able to resolve wpad.example.com and request the WPAD file.
Verify your Firewall configuration
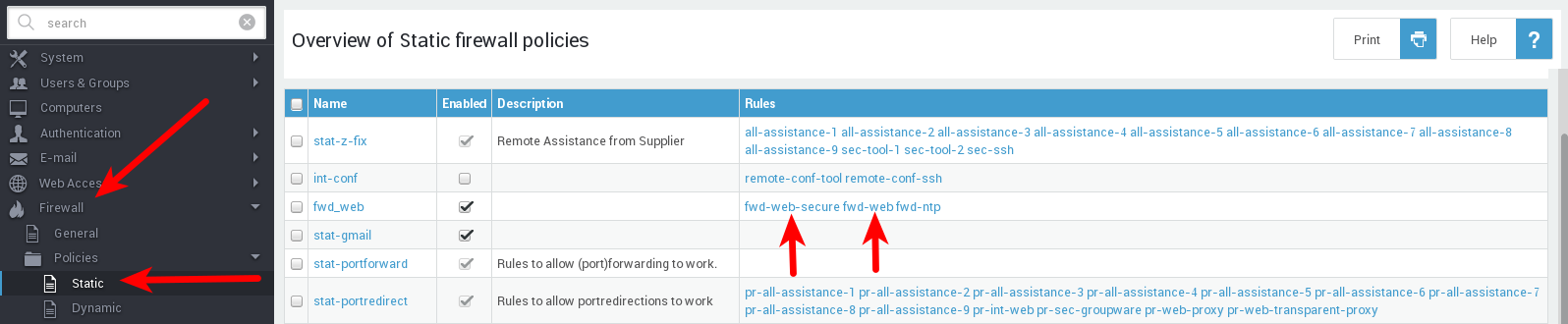
Ensure clients cannot connect directly to the Internet, but only via the AXS Guard proxy.
Check your static firewall policies and ensure fwd-web and
fwd-web-secure rules are disabled.
If there are any static firewall policies in place that where these rules are enforced, disable or remove the policies or remove the rules from the policies.
If there are users or systems which need direct access to the Internet, create a dynamic firewall policy and assign it to the appropriate user.
Verify the Proxy Redirection Configuration
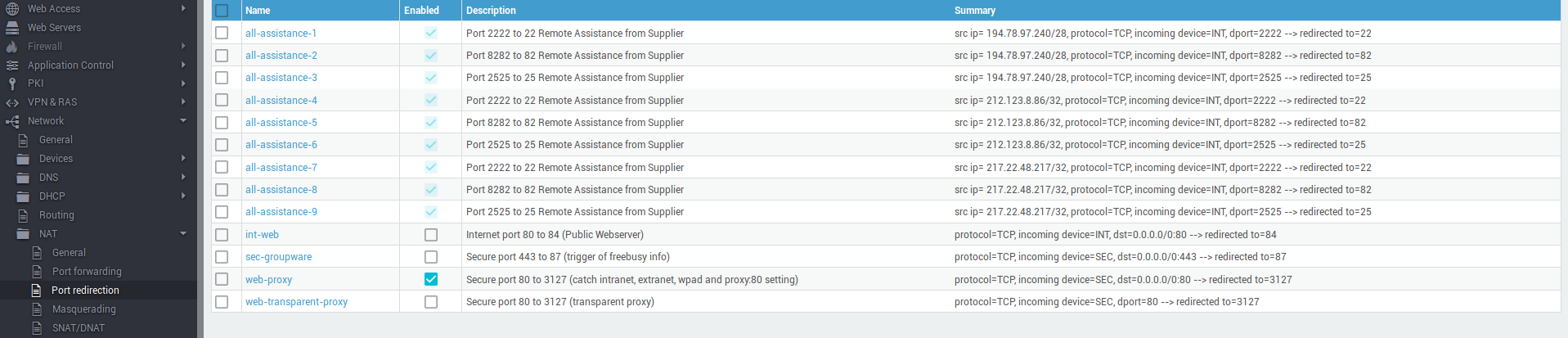
For automatic proxy detection to work, port redirection must be correctly configured on the appliance:
-
Go to Network > NAT > Port Redirection
-
Verify that the port redirection
web-proxyrule is enabled. If not, enable it. -
Verify that the port redirection
web-transparent-proxyrule is disabled. If not, disable it. -
Assign appropriate Web Access ACLs to your users, groups or computers.
Important
Enabling both port redirections rules will cause unwanted behavior.
By default, a system-wide ACL is enforced for all users, groups and computers. Go to Web Access > Proxy Server to select the appropriate system-wide ACL.
User-specific ACLs have priority over group-specific ACLs, which in turn have priority over computer-specific ACLs. Each of these, when enabled, overrule the system-wide web access ACL.
Using your own DHCP and DNS Servers
Considerations
If you are not using the AXS Guard DHCP and DNS services, our support team will not be able to configure the settings for you.
There are three important steps to consider if you decide to use the DNS option:
-
Create an A record for your AXS Guard appliance in the forward lookup zone of your domain.
-
Create a WPAD CNAME record which points to the A record created in step 1.
-
Create a PTR record for your AXS Guard appliance in the reverse lookup zone of your domain.
Microsoft DNS
If you are using a Microsoft Windows server, use the dnscmd command,
which is a command-line interface for managing DNS servers:
Check whether the global query blocklist is enabled:
dnscmd /info /enableglobalqueryblocklist
To show the hostnames in the current blocklist, use the following command:
dnscmd /info /globalqueryblocklist
To unblock name resolution for hostnames in this list, use the following command:
dnscmd /config /enableglobalqueryblocklist 0