Blocking Apps
Introduction
About this Document
This document provides instructions for system administrators on how to block certain apps and services. While we will use TikTok as an example, the instructions provided in this document can also be used to block other applications and services.
Dangerous Apps
Certain apps can be considered dangerous for various reasons, depending on how they handle user data or content. In the case of TikTok, concerns have been raised about its data privacy practices, as well as its content moderation policies.
TikTok collects a significant amount of data from its users, including location data, device information, and browsing history, which can be used for targeted advertising or other purposes. There have also been concerns about potential censorship or bias in its content moderation practices, as well as its handling of user-generated content that may be inappropriate or harmful.
Furthermore, TikTok's ownership and connection to the Chinese government have raised concerns about potential data sharing or surveillance, which has led to some countries banning or restricting its use in certain contexts.
Overall, it's important for users to be aware of the risks associated with any app they use and to make informed decisions about their privacy and security.
Blocking Methods
The supported blocking methods are listed by order of preference: system administrators can use application control, advanced firewall rules, add an application filter to the proxy server's ACL, create a DNS filter or configure DNS sinkholes to block the application. Select the method that best suits your network environment.
Please be aware that some methods come with their own set of caveats. We recommend that you carefully review the details of each method before making a decision.
Application Control
The system's default application control policy allows HTTP, HTTPS and DNS traffic, while blocking other types of traffic, including access to social media. Therefore, no additional configuration should be necessary.
System administrators can easily verify the list of blocked applications and services in application control policies:
- Log in to your AXS Guard appliance.
- Navigate to Application Control > Policies.
- Click on the appropriate policy name, e.g.
system, to view the blocked applications. - Make sure that the policy is correctly assigned.
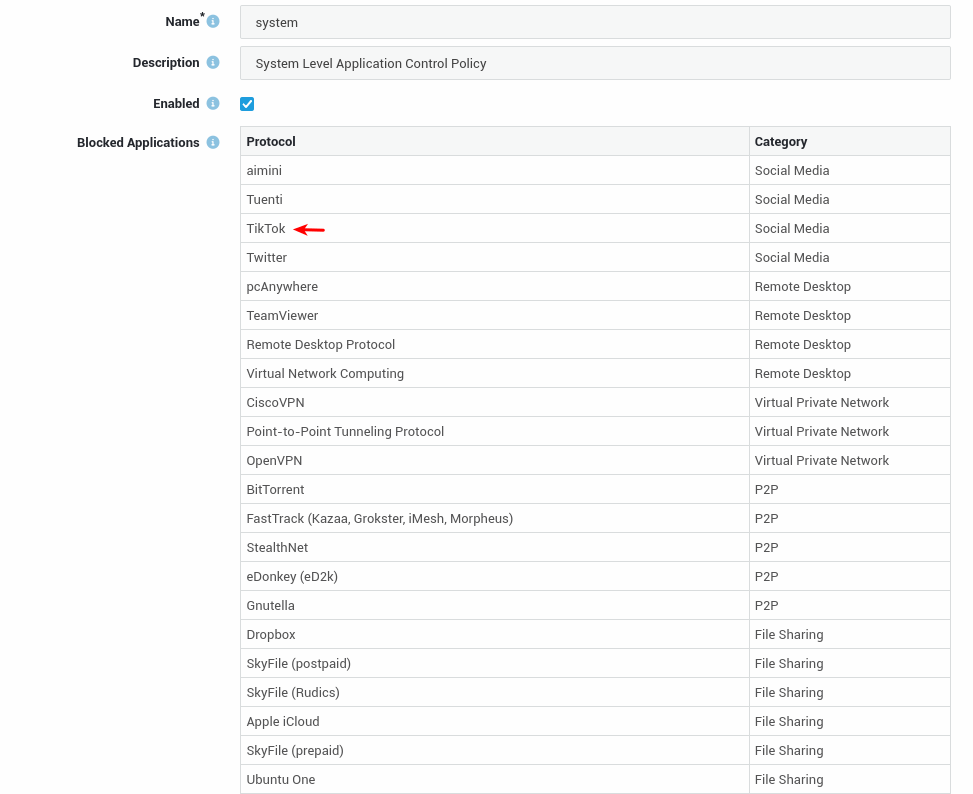
Application Control Test
Log in to a computer and execute the following curl command:
curl -I https://www.tiktok.com
TikTok is blocked by the factory default policy and should return the following response:
curl: (35) OpenSSL SSL_connect: Connection reset by peer in connection to www.tiktok.com:443
Firewall Configuration
- Log in to your AXS Guard appliance.
- Navigate to Firewall > Rules > Advanced.
-
Add the following lines to the rules field:
-v -t filter -I FORWARD -m string --string "tiktok" --algo kmp --icase -j REJECT -v -t filter -I FORWARD -m string --string "musical.ly" --algo kmp --icase -j REJECTor
-v -t filter -I FORWARD -p tcp --dport 443 -m string --hex-string "|74696b746f6b|" --algo kmp --icase -j REJECT -v -t filter -I FORWARD -p tcp --dport 443 -m string --hex-string "6d75736963616c2e6c79" --algo kmp --icase -j REJECT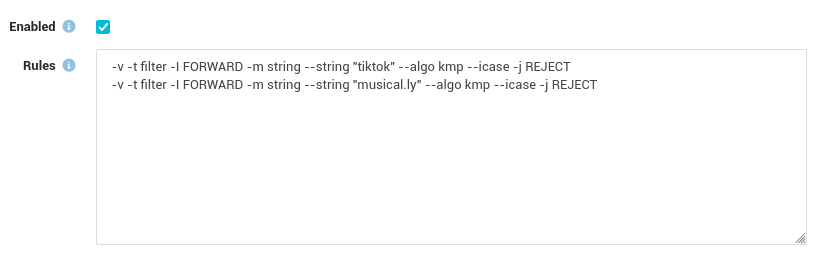
-
Save your configuration.
The iptables parameters shown above insert new rules into the FORWARD chain that match packets containing the strings tiktok and musical.ly using the Knuth-Morris-Pratt algorithm.
When a packet matches one of these rules, it will not be forwarded to its destination. Please note that no logging will be performed in this case.
Important
The iptables rules provided above filter all packets that contain the strings "tiktok" and "musical.ly" in the payload and reject them. It's important to carefully consider the potential pitfalls and unintended consequences of using these rules, and weigh the benefits against the risks before implementing them in a production environment. While these rules might be useful in some cases, they have several potential pitfalls:
-
False positives: If any legitimate traffic also contains the string "tiktok" in the payload, then that traffic will be rejected as well. For example, if a website's domain name contains the word "tiktok", the website might be blocked.
-
Performance impact: Using the
-m stringoption to search for a specific string in the packet payload can be CPU intensive, and may impact the performance of the system, especially if the rule is applied to a high volume of network traffic. -
Obfuscation: It's possible for someone to obfuscate the string "tiktok" in the packet payload to bypass the rule, rendering it ineffective.
-
Legal implications: Depending on the jurisdiction and context, blocking certain traffic, such as TikTok, may have legal implications, and could be considered censorship or discriminatory. It's important to consider the legality and ethical implications of blocking specific types of traffic before implementing such rules.
Firewall Test
Log in to a computer and execute the following curl commands:
curl -I https://www.tiktok.comcurl -I https://www.musical.ly
Both commands should result in an error:
curl: (35) error:0A000126:SSL routines::unexpected eof while reading
If users attempt to access TikTok with a browser, they will see a connection failure, as shown in the image below:
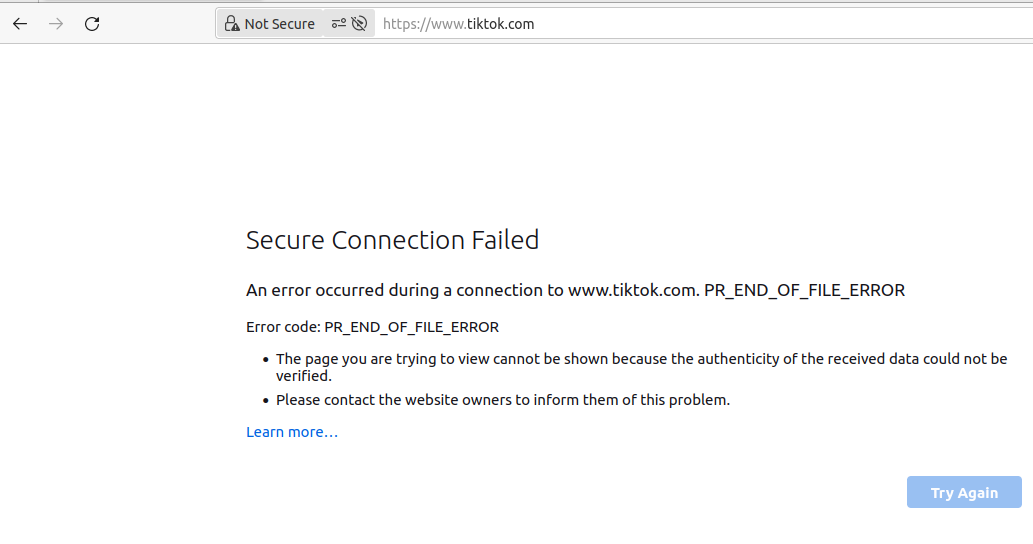
Pitfalls of IP Address Blocking
Blacklisting application IP addresses with a firewall block list is not an effective solution for several reasons.
Apps and services like TikTok use a large number of IP addresses that can change frequently without prior notice, so it may be challenging to maintain an accurate and up-to-date list of all IP addresses. It is important to note that the IP addresses obtained through the WHOIS database may not represent a complete list, and should not be relied upon as the sole source of information.
Furthermore, blocking TikTok's IP address range might also block access to other legitimate services that share the same IP addresses or subnets. Therefore, blocking IP address ranges is not the most effective solution in such scenarios.
Proxy Configuration
- Log in to your AXS Guard appliance.
- Go to Web Access > Filters > Lists.
-
Create a new site list with the following wildcard expressions:
*tiktok* *musical.ly* -
Create a category and add the new site list to it.
- Add the new category as a blocked item to the desired ACL, e.g.
predef-no-porn. - Make sure that the ACL is assigned to the appropriate users, groups and computers. To enforce the ACL system-wide, navigate to Web Access > Proxy Server.
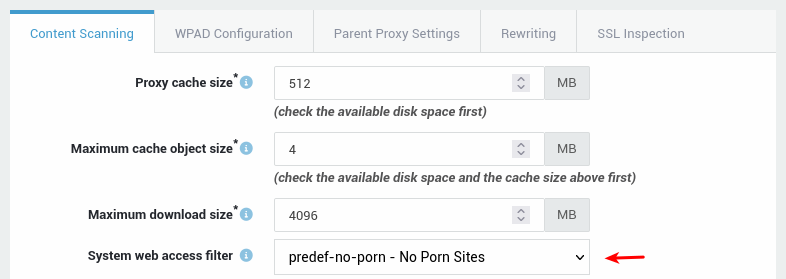
Proxy Test
Log in to a computer and execute the following curl command:
curl -I -x http://192.168.250.254:3128 https://www.tiktok.com -U axsguard_username:axsguard_password | grep -wo blocked
The command should show the request as blocked:
curl: (56) CONNECT tunnel failed, response 302
blocked
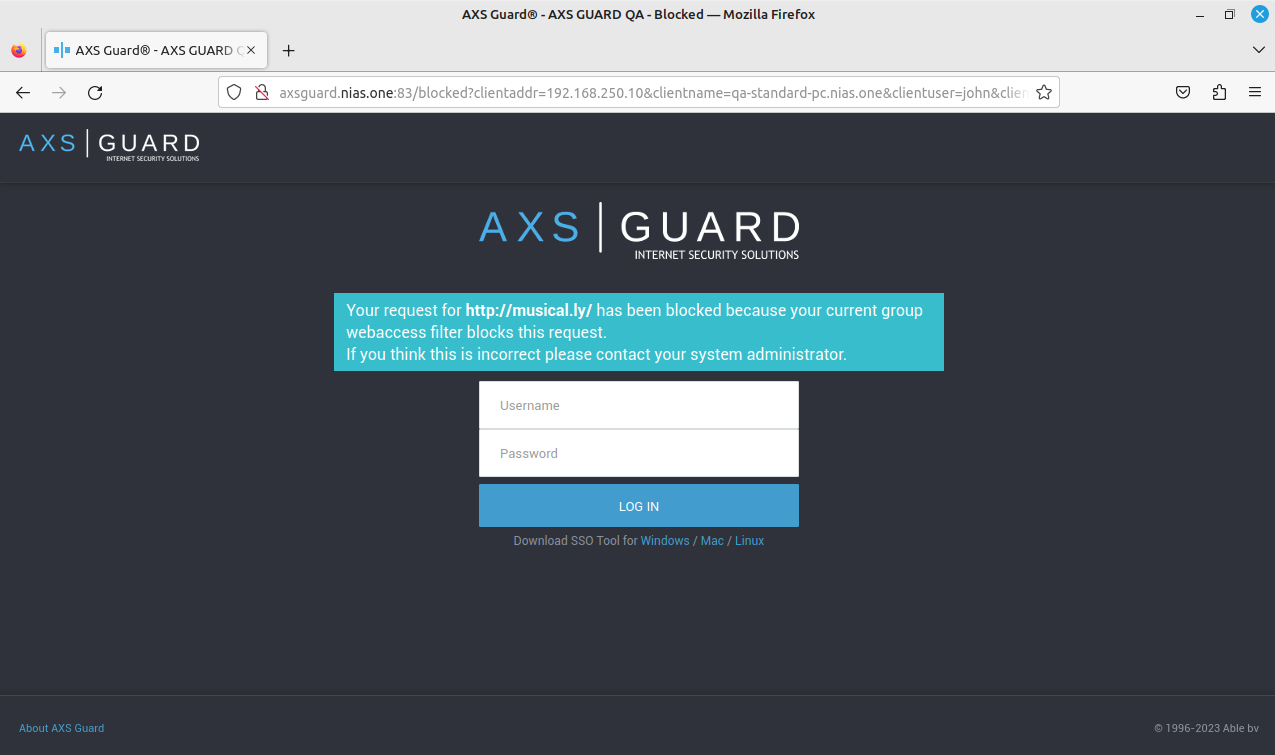
If users attempt to access TikTok with a browser, their request will be blocked, as shown in the image below:
DNS Filters
AXS Guard allows system administrators to block NSFW content with DNS filters.
The main purpose of DNS filters is to enforce internet usage policies, enhance security, and protect against malicious or inappropriate content. They offer organizations a way to manage and regulate internet access for their users.
See the DNS security documentation for additional information and configuration instructions.
It should be noted that mobile apps like TikTok ship with DNS blocking circumvention and may require a more aggressive approach.
DNS Sinkholes
This method will work for browser-based traffic if all DNS requests in your network are being handled by AXS Guard. Also see the section about blocking rogue DNS traffic on this site for additional information.
It should be noted that mobile apps like TikTok ship with DNS blocking circumvention and may require a more aggressive approach.
- Log in to your AXS Guard appliance.
- Go to Network > DNS > Forwarding.
-
Create DNS sinkholes for the following domains:
tiktok.com tiktokv.com tiktokcdn.com tiktok.be musical.ly dns.google.com bdurl.net 4.1.107.203.in-addr.arpa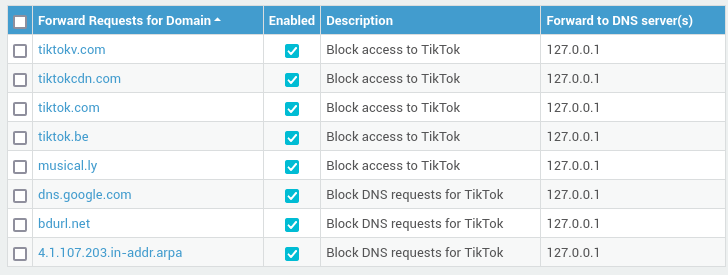
-
Save your configuration.
DNS Test
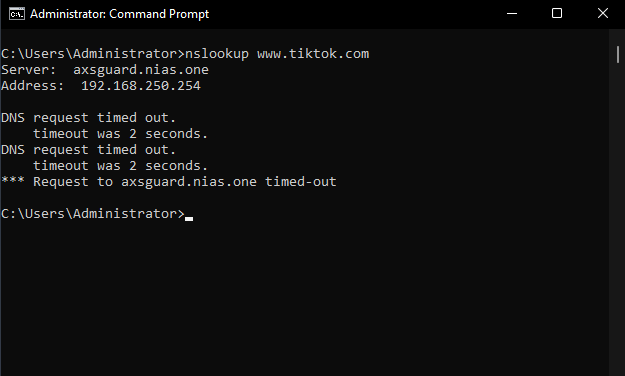
Log in to a computer, open a command prompt and execute the following command to test your configuration:
nslookup www.tiktok.com
The request should time out, as shown in the example below:
Limitations and Considerations Regarding App Blocking
Please note that blocking TikTok or other apps on a specific device or network only applies to that device or network. Additionally, it's important to keep in mind that there are ways to bypass the block, such as using a VPN or a Tor browser.