Blocking SSO to prevent VPN disconnect issues
Introduction
About this Document
In this document we explain how to prevent accidental logouts when using the SSO tool in combination with AXS Guard VPN services. This document was last updated on 03/11/2019.
About the SSO Tool
The SSO Tool is a desktop application that can be installed on Windows, Linux and Mac.
The application is used for authentication against AXS Guard and activates a set of dynamic firewall policies and proxy ACLs assigned to the user. See the SSO manual on this website for additional information.

VPN Authentication
About
When connecting to the corporate network via a VPN, user authentication occurs while the VPN connection is established, typically with a username/password combination, sometimes with a client certificate. The required method is enforced by the selected AXS Guard authentication policy or by the type of VPN service being used.
The example below shows the authentication logs when connecting with an OpenVPN client and after logging out.

Why you shouldn’t use SSO with a VPN Connection
When users are connected to an AXS Guard VPN service, they are already authenticated; there is no need for extra authentication, e.g. using the SSO tool.
Doing so will have undesirable effects.
When a VPN connection is established, the SSO tool may automatically connect to the AXS Guard appliance using the same credentials as those used for the VPN. When this happens, the AXS Guard authentication server will detect the new login attempt made by the SSO tool and log the user out. As a result, the user’s authenticated VPN session will be terminated.
Dynamic firewall policies loaded for the VPN connection will be unloaded and the user won’t be able to access the configured network resources. The example below shows the authentication logs after logging in with the SSO tool during an OpenVPN session.

How to prevent SSO from disconnecting authenticated VPN sessions
The easiest way to block the SSO tool from accessing AXS Guard over a VPN connection is by configuring a static firewall policy:
-
Create a towards firewall rule that blocks access to port 3129 on AXS Guard.
-
Create a new static firewall policy and add the previous rule to this policy.
-
Place the newly created policy above the
stat-secfirewall policy.
Step 1
-
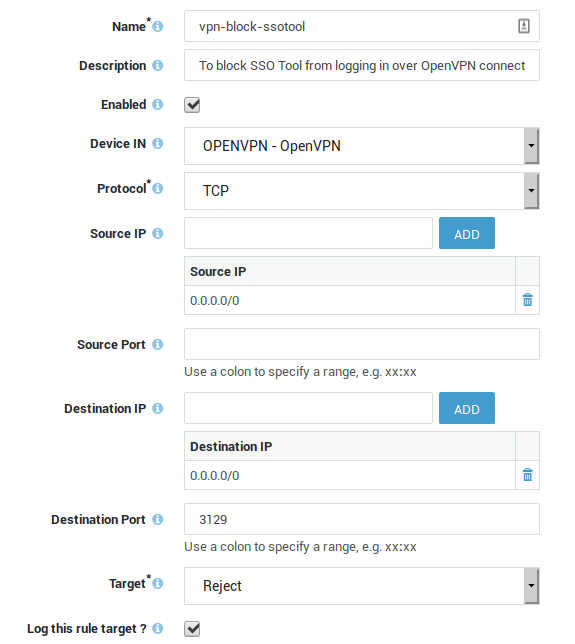
Go to Firewall > Rules > Towards
-
Add a new firewall rule.
-
Enter a name for the rule, e.g.
vpn-block-ssotooland use the following settings:-
Device = OpenVPN
-
Protocol = TCP
-
Destination Port = 3129
-
Target = Reject
-
Log the rule target so blocks appear in the firewall logs.
-
-
Click on save.
Step 2
-
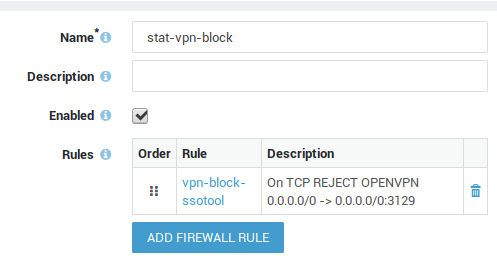
Go to Firewall > Policies > Static
-
Add a new policy.
-
Enter a name for the policy, e.g.
stat-vpn-block. -
Add the newly created rule to the firewall policy.
-
Click on save.
Step 3
Since the stat-sec policy contains a rule which allows connections to
port 3129, you have to make sure that the newly created policy precedes
this policy. See the firewall guide for additional information on this
subject.
-
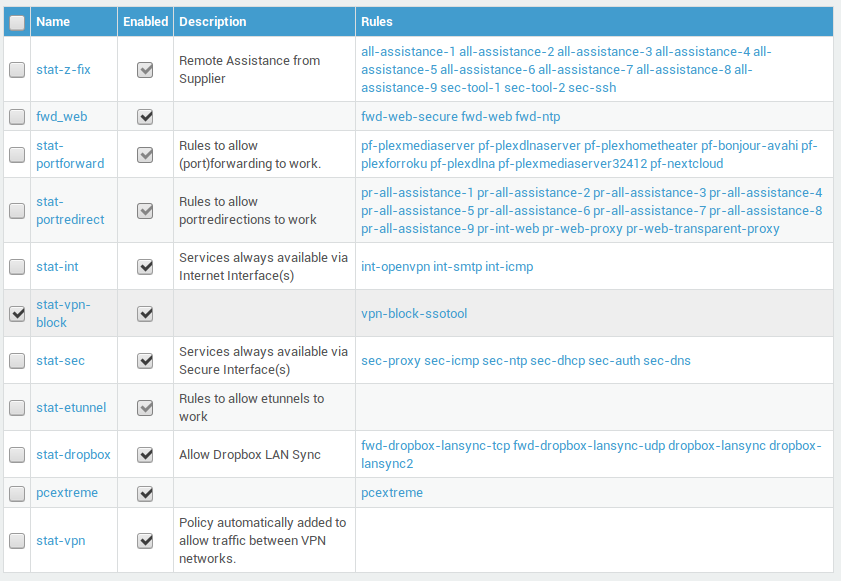
Go to Firewall > Policies.
-
Tick the checkbox next to the newly created policy, e.g.
stat-vpn-block. -
Place the new policy above the
stat-secpolicy (using the up and down arrows in the GUI).