Connecting with Azure
Introduction
About this Document
This document explains how to connect the AXS Guard IPsec server with Microsoft Azure VPN using PSK host authentication.
Before you start
Azure VPN offers both policy-based and route-based IPsec tunnels, both of which are supported by the AXS Guard appliance.
The configuration of the Azure platform is beyond the scope of this guide. For information about setting up your tunnels on Azure, please refer to the official documentation provided by Microsoft.
Default IPsec & IKE parameters
You can find the supported combinations of algorithms and parameters that Azure VPN gateways use on the official Azure VPN documentation website.
Azure-side Configuration Overview
-
Configure the Microsoft Azure virtual network.
-
Configure the Microsoft Azure DNS server.
-
Create the Microsoft Azure virtual network gateway.
-
Create the Microsoft Azure local network gateway.
AXS Guard-side Configuration
Policy-based Setup
-
Go to VPN > IPsec > Tunnels
-
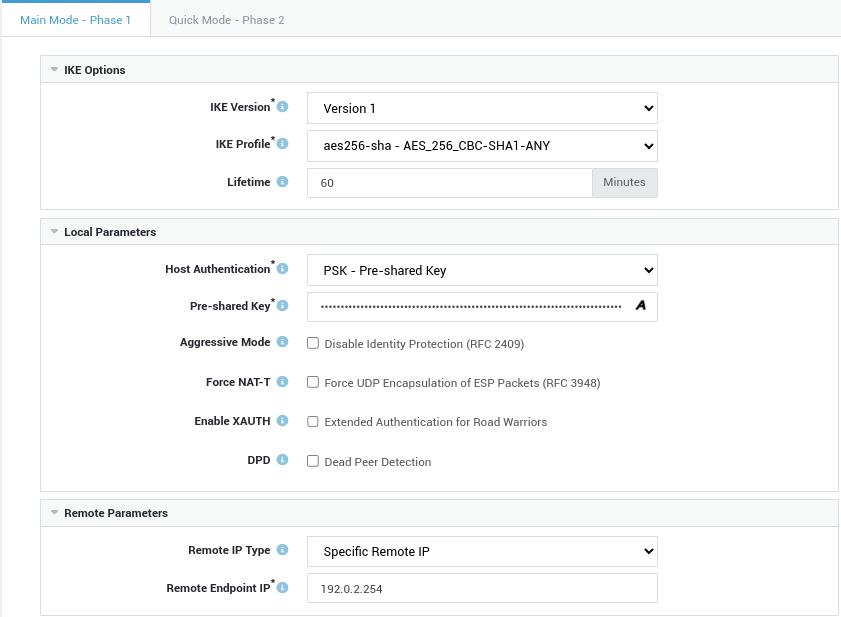
Create a new tunnel with the following phase 1 settings:
-
IKE Version:
Version 1. -
IKE Profile:
aes256-sha - AES_256_CBC-SHA1-ANY. -
Host Authentication:
PSK. -
Remote IP Type:
Specific.
-
-
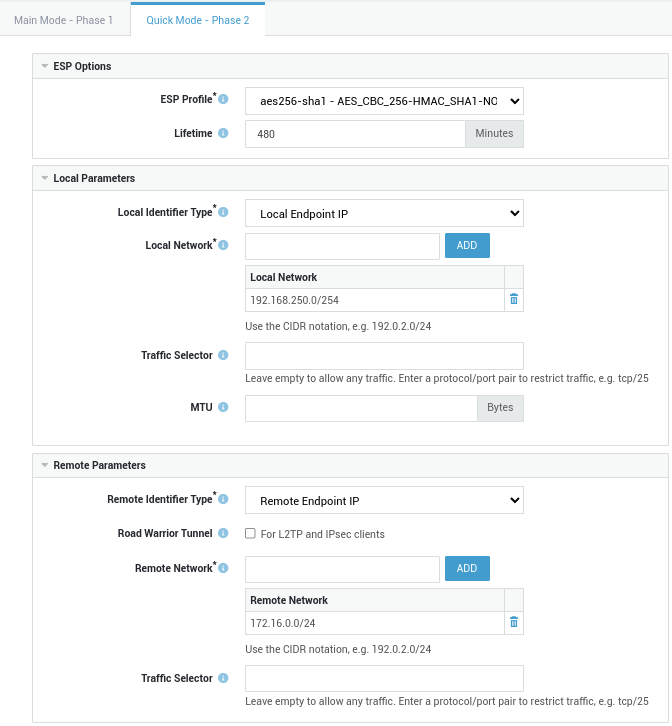
Configure the following phase 2 settings:
-
ESP Profile:
aes256-sha1 - AES_CBC_256-HMAC_SHA1-NONE. Note that PFS is disabled in this profile. -
Remote Identifier Type:
Remote Endpoint IP.
-
Route-based Setup
-
Go to VPN > IPsec > Tunnels
-
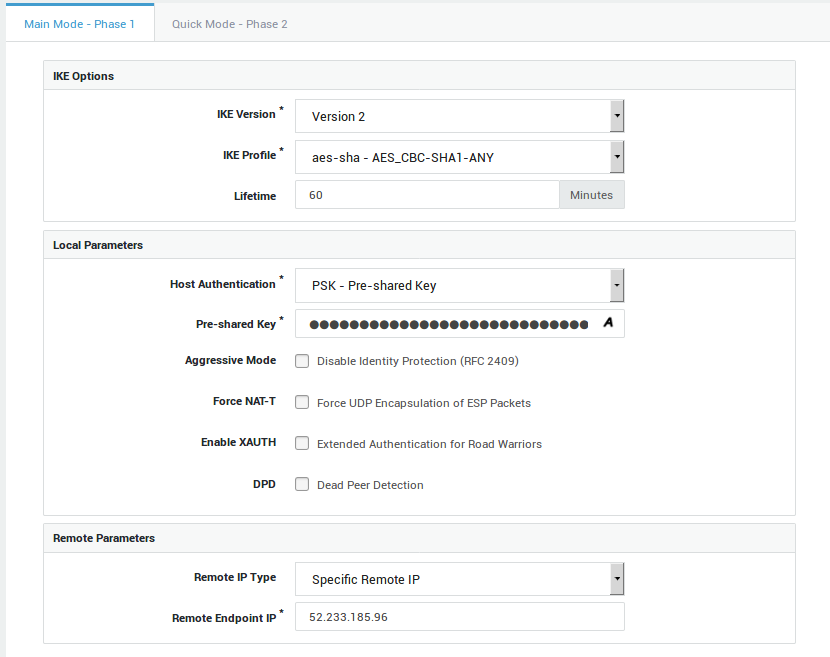
Create a new tunnel with the following phase 1 settings:
-
IKE Version:
Version 2. -
IKE Profile:
AES_CBC-SHA1-ANY. -
Host Authentication:
PSK. -
Remote IP Type:
Specific.
-
-
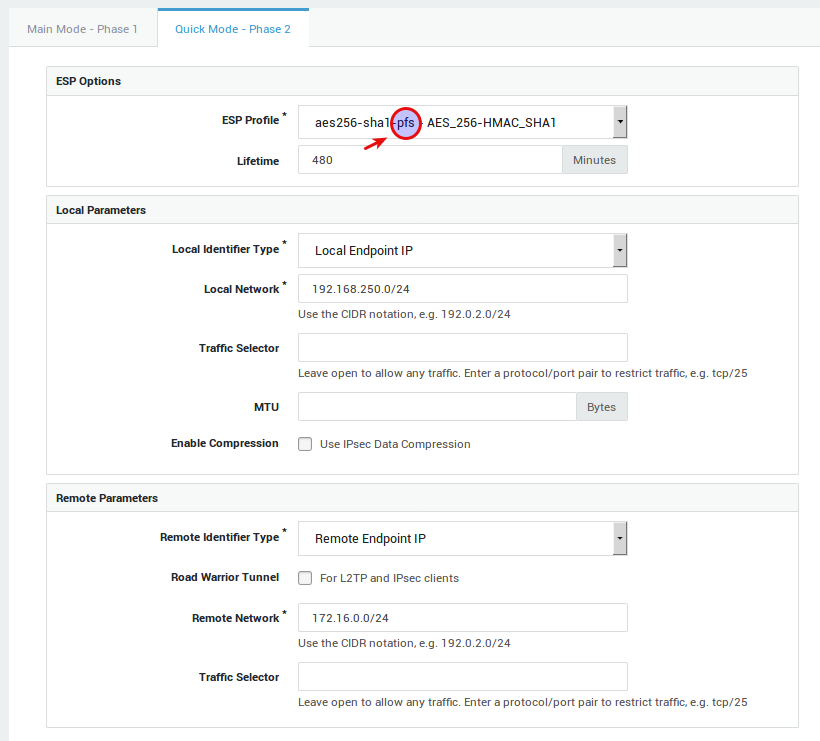
Configure the following phase 2 settings:
-
ESP Profile:
AES_256-HMAC_SHA1. Note that PFS is enabled in this profile. -
Remote Identifier Type:
Remote Endpoint IP.
Important
Both sides of the VPN must be able to support PFS in order for PFS to work. When PFS is enabled, the two gateways must generate a new set of phase 1 keys for every negotiation of a new phase 2 SA.
-