Version 11.2
11.2.4
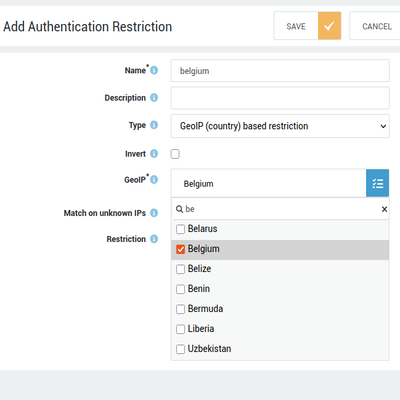
User Authentication
- Added support for country-based authentication restrictions.
-
User authentication can now be allowed or blocked based on geographic location.
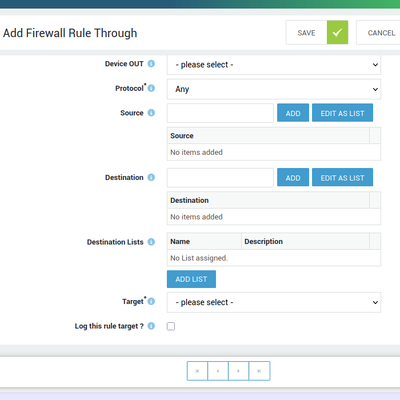
Firewall Rules
- Added the option to filter traffic based on geographic location.
-
Blocking network traffic to and from specific countries or regions can significantly reduce the attack surface.
Administrator Tool
- Device status page: You can now filter on device type.
-
The process groups on the statistics page are now sorted.
Miscellaneous
- Entra ID sync now converts all usernames to lowercase.
- Decreased the timeout for directory services synchronization.
- Added the "friendly name" attribute to OpenVPN certificates for Windows 11 clients.
- SecureDNS: Emails matching a botnet or APT signature are now quarantined for review.
- Enhanced mail whitelisting capabilities.
11.2.3
Firewall Enhancements
- Outdated DNS query results are no longer retained in firewall rules.
- Resolved a race condition when loading combinations of FQDN-based and static rules.
- Firewall rules associated with non-existent devices now correctly fail to match network traffic.
- Enhanced the synchronization mechanism for cloud-based firewall rules.
Bug Fixes
- Updated multiple software packages to remediate recent CVEs.
- Improved email scanning capabilities to inspect additional headers for known malicious domains.
- Fixed a race condition that could cause DNS server failures when OpenVPN was misconfigured.
11.2.2
Bug Fixes
- Fixed an issue where the source exclude fields in firewall and port redirection rules were missing from system backups.
- Addressed an issue in the DKIM signing service that could lead to the blocking or flagging of legitimate emails.
- Resolved an issue that limited the maximum number of users allowed in authentication restrictions.
- Ensure that user and group authentication restrictions are correctly enforced after creation or modification.
11.2.1
Bug Fixes
- Improve connection stability towards AXS Guard cloud.
- Reconfigure VLAN devices when an IP alias changes.
- Remove unwanted security event errors related to statistics gathering.
- Correctly handle specific output device usage in firewall rules.
11.2.0
This document provides crucial information regarding the upgrade to AXS Guard version 11.2.0. Please review it carefully to ensure a smooth transition and prevent service disruptions.

Timing & Considerations
- The upgrade process is estimated to take approximately 30 minutes.
- To minimize service interruptions, we strongly recommend to schedule this upgrade during off-peak hours or a designated maintenance window.
- Please communicate this scheduled downtime to your users in advance.
- During the upgrade, the system will be temporarily unavailable.
-
Go to Software Updates > Software Packages to install the new version.
Key Feature Enhancements
UEFI Support
- AXS Guard now supports Unified Extensible Firmware Interface (UEFI) boot.
- This modern standard offers improved security, faster startup times, and enhanced compatibility with newer hardware.
- This transition eliminates reliance on legacy BIOS boot and enables installation on UEFI-enabled virtual machines using a virtual CD or USB drive.
- For new virtual installations, configuring UEFI boot is highly recommended.
- If you already have an existing installation, a fresh installation is required to enable UEFI support.
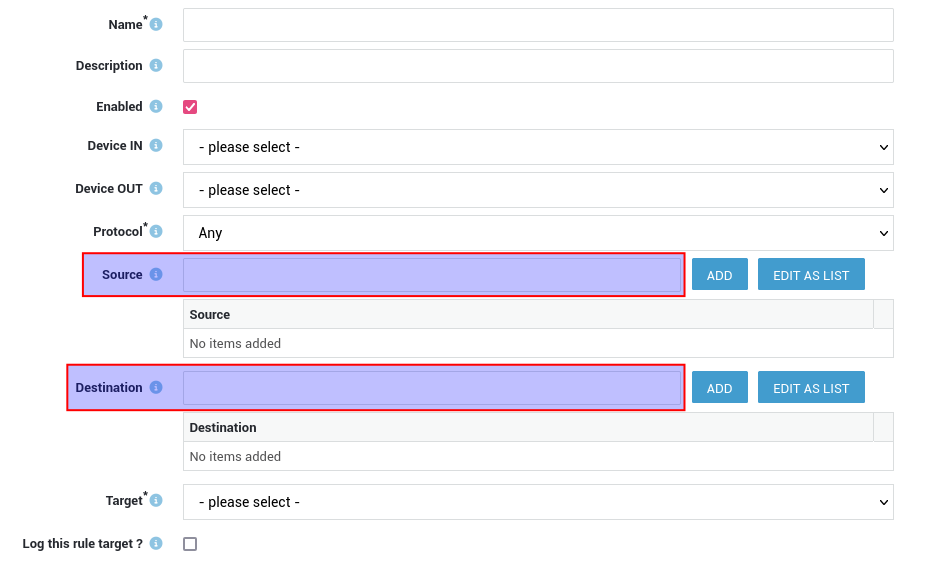
Firewall Rule FQDN Support
We enhanced FQDN support for firewall rules, which offers greater flexibility and control over network traffic. Enhancements include:
- FQDN support for DMZ filter rules, simplifying access management for servers in your DMZ.
- FQDN support for port forwards, streamlining traffic forwarding to internal servers based on domain names.
- FQDNs can be used as both the source and destination in "towards" rules, allowing granular control over traffic originating from or directed to specific domains.
- FQDNs can be used as both the source and destination in "through" rules, enabling precise filtering of traffic passing through the firewall based on domain names.
Mail System Enhancements
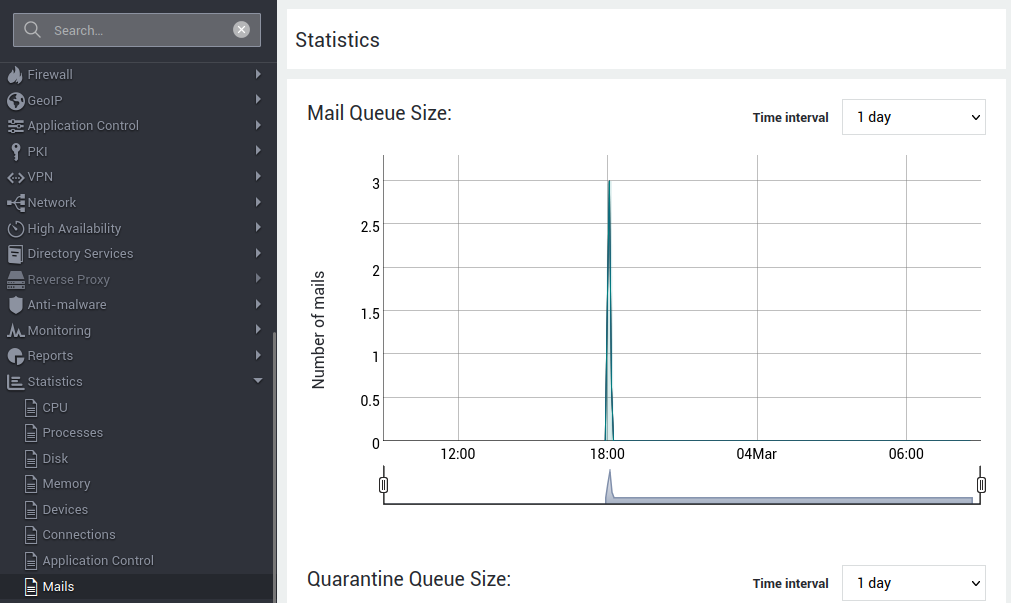
Mail Statistics
A new statistics page has been implemented, providing time-series data for key mail server metrics. This allows administrators to monitor performance and identify potential issues. The new statistics page offers insights into:
- Mail Queue size: Track the volume of emails waiting to be sent.
- Quarantine Queue size: Monitor the number of emails held for review.
- Mail Delay: Analyze the time it takes for emails to be delivered.
- Mail Status: Gain an overview of the mail server's operational status.
Improved DMARC Checking
DMARC (Domain-based Message Authentication, Reporting & Conformance) verification now influences the spam score of incoming emails. This significantly enhances spam detection accuracy and reduces the risk of phishing attacks.
IMAP & POP Performance
To improve mail processing times, the I/O load on high-volume mail servers can be reduced by enabling additional RAM caches.
Additional Fixes
- Sorting on the "Mail Quota Status size" has been rectified.
- The mail size on the "Mail Queue size" page is now human-readable.
- When exporting the mail quota status page, the exported size is now in bytes instead of a human-readable string.
System Package Updates
Over 250 software packages have been updated to address security vulnerabilities and ensure the software remains current. These updates include bug fixes, performance improvements, and security patches, contributing to a more stable and secure system.
Discontinued Features
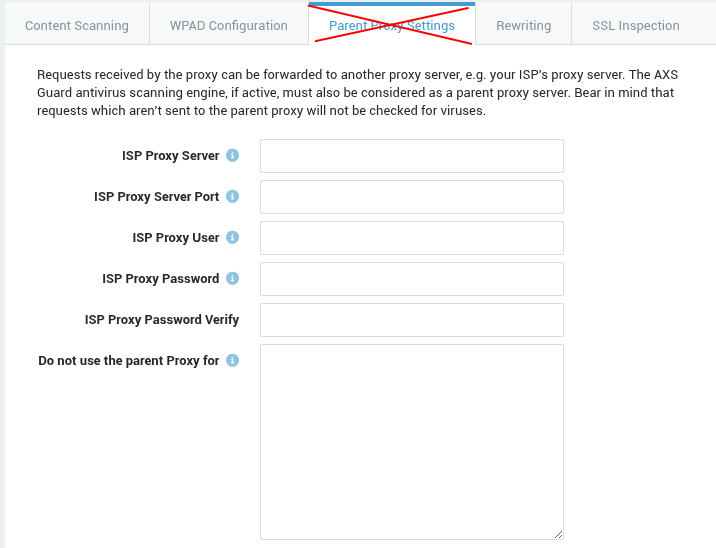
Parent Proxy for Web Access
Support for the Parent Proxy functionality has been discontinued.
Fax Module
Fax support has been completely removed. We recommend evaluating modern communication methods as a replacement for faxing.