Application Control
Introduction
About this Document
This document is a reference source for technical personnel, system administrators and network administrators who are looking to secure their network at the application level.
Examples used in this Guide
All setups and configuration examples in this guide are executed as an advanced administrator. Some options are not available if you log in as a full administrator or a user with lower access privileges.
As software development and documentation are ongoing processes, the screenshots shown in this guide may slightly deviate from the latest user interface.
Application Control Concepts
About
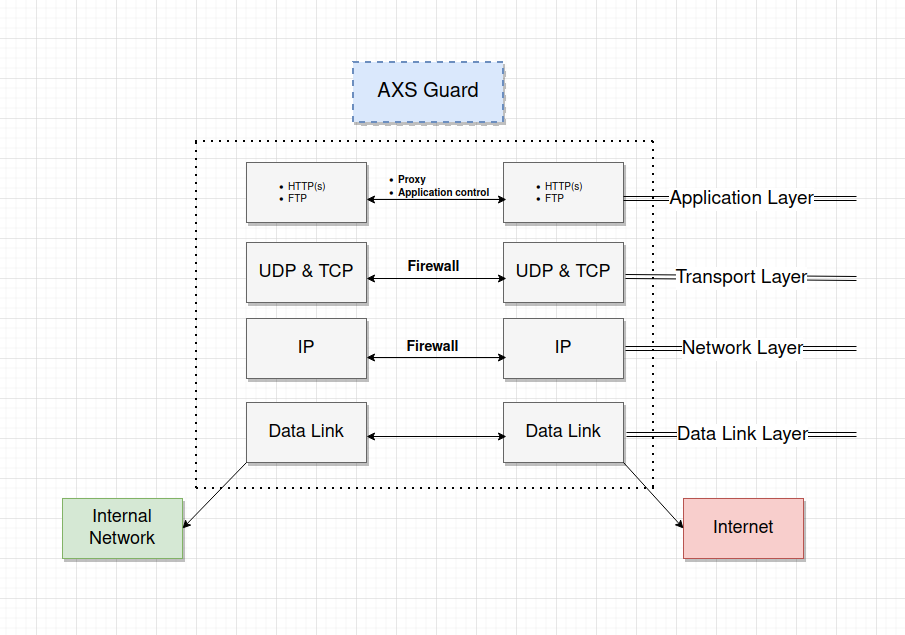
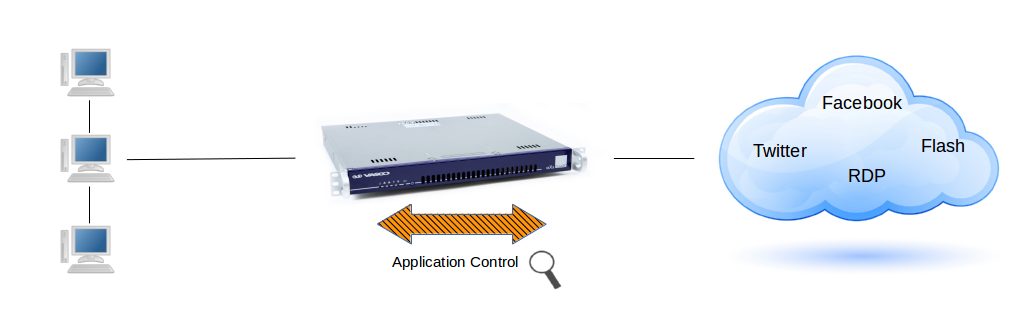
Application control refers to the process of managing and controlling network traffic related to the execution of certain software programs and access to applications on the Internet. This can include allowing certain applications and protocols to be used while blocking others, e.g. Facebook, Twitter, etc.
Its goal is to increase network security and efficiency by limiting the network resources consumed by unnecessary or resource-intensive programs.
Traffic Matching
The application control system allows application-layer detection of protocols, regardless of the port being used.
This means that it is possible to both detect known protocols on non-standard ports, e.g. HTTP traffic on ports other than 80, and also the opposite, e.g. to detect Skype traffic on port 80. The system can also detect and block access to given file types, such as certain multimedia files.
Key Benefits
The key benefit of the application control system is that it can "understand" a vast amount of applications and protocols, such as FTP, DNS, RDP or simple web browsing, and is able to detect whether an unwanted protocol is being sneaked through on a non-standard port or whether a protocol or file is being abused in any harmful way.
It allows system administrators to swiftly block certain types of network traffic and files which are harder or impossible to block via the standard firewall and the proxy server. See the examples below.
Example 1: Layer 4 vs Layer 7 DoS Attack
A Layer 4 DoS attack is often referred to as a SYN flood. It works at the TCP layer.
A TCP connection is established in what is known as a 3-way handshake. The client sends a SYN packet, the server responds with a SYN ACK, and the client responds to that with an ACK. After the "three-way handshake" is complete, the TCP connection is considered established. It is as this point that applications begin sending data using a Layer 7 or application layer protocol, such as HTTP.
A Layer 7 DoS attack is a different beast and it’s more difficult to
detect. A Layer 7 DoS attack is often perpetrated through the use of
HTTP GET. This means that the 3-way TCP handshake has been completed,
thus fooling devices and solutions which are only examining layer 4 and
TCP communications. The attacker looks like a legitimate connection, and
is therefore passed on to the web or application server.
Example 2: Flash Player Vulnerabilities
Some versions of Adobe Flash Player allow remote attackers to execute
arbitrary code via crafted .swf content or to perform DoS attacks. The
impact is severe.
In some cases there is a total information disclosure, resulting in all system files being revealed. These vulnerabilities also compromise the integrity of targeted systems. An attacker can also render systems completely unavailable.
Application Categories
The following application types can be blocked:
-
Social Media, e.g. Facebook, Twitter
-
Remote Desktop, e.g. RDP and VNC
-
VPN, e.g. PPTP
-
P2P, e.g. Bittorrent
-
File Sharing, e.g. Dropbox
-
Messaging and VoIP, e.g. Skype, Viber
-
Multimedia, e.g. Spotify, YouTube, avi files
-
Others, e.g. Gmail, FTP
Situation in the Network Stack
-
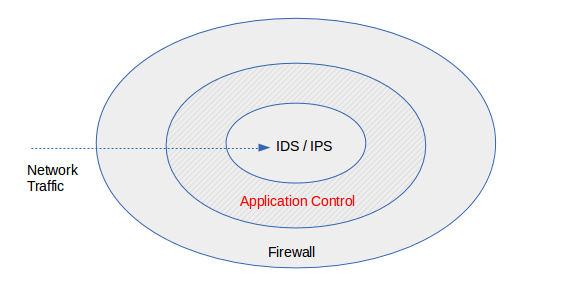
Only traffic that is specifically allowed by the AXS Guard firewall and defined in the application control policies is verified.
-
Traffic which is allowed by application control rules can still be blocked by the AXS Guard IPS, if the feature is enabled and configured on your appliance. Adjust your IPS configuration if necessary.
-
Application control checks the payload of network packets and acts upon detection of patterns in these packets, which means that it checks established connections.
-
Clients which connect to the Internet via the AXS Guard proxy server to browse the Internet are subject to the application control policy assigned to the proxy server; computer, group-level and user-level application policies are not enforced in this case.
Policy-based Management
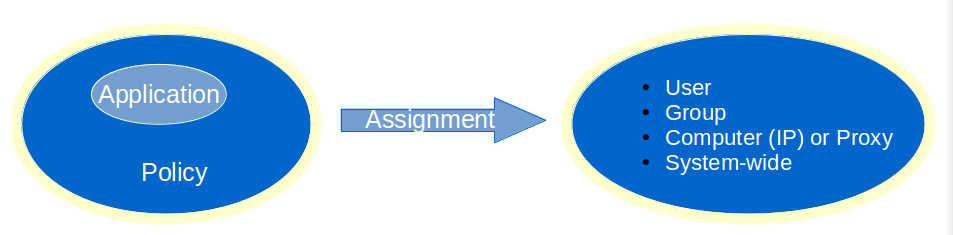
Application control policies govern application access rights of users connected to your network, for example, whether a user may or may not access Facebook, Twitter, etc.
Policy Levels
Policies can be assigned at the following levels:
-
System-wide policies are authentication-independent and apply to all users, computers and other devices connected to the appliance. These policies must be as restrictive as possible to avoid possible abuses in your network.
-
Computer policies are authentication-independent and are associated with a given IP address in your network, e.g. to allow a server to connect to the Internet to perform automatic updates. Computer policies should be used sparingly and only in cases where user authentication is not possible.
-
Group policies are authentication-dependent and affect the members of a group, e.g. whether or not the members of a given group are allowed to connect to Facebook.
-
User policies are authentication-dependent and affect a single user, e.g. to override a group, computer or system-wide policy, e.g. all members of a group have access to Facebook, except a specific member of the group.
Internet Access via the Proxy Server
Clients which connect to the Internet via the AXS Guard proxy server are subject to the application control policy assigned under Web Access > Proxy Server. Computer, group-level and user-level application policies are not enforced in this case.
VPN Traffic
Separate application control policies can be configured for VPN clients. If none are configured, the system-wide policy will be enforced by default. For more information and configuration instructions, please refer to the VPN guides available on this site.
System Defaults
Important
- The system default application control policy allows HTTP, HTTPS and DNS traffic. Other traffic is blocked by default, e.g. access to social media.
- Ideally, system-wide and computer-level policies should block all applications. Access to applications and services should only be allowed after successful authentication.
- The system-wide policies apply to all traffic to and from the AXS Guard appliance, including VPN traffic. Traffic to and from the web-based administrator tool and SSH traffic are always allowed.
Logging and Statistics
The AXS Guard application control system offers the option to log all dropped traffic. It also offers detailed traffic statistics per category through the use of simple filters.
Application Control Configuration
Feature Activation
-
Log on to the AXS Guard appliance as explained in the System Administration guide.
-
Go to System > Feature Activation.
-
Expand the Firewall option and check
Do you use the AXS Guard Application Control Service?and update your configuration.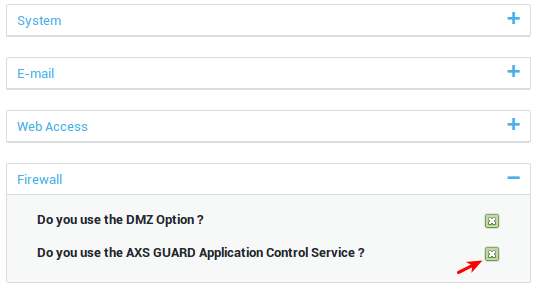
Creating Application Control Policies
-
Go to Application Control > Policies.
-
Click on the
+button (add new). -
Enter the parameters as explained in the table below and save your configuration.
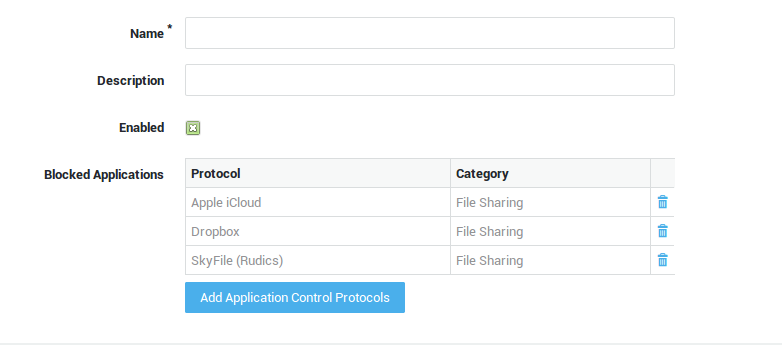
| Option | Description |
|---|---|
Name |
Enter a name for the application policy. |
Description |
A policy description (optional field). |
Enabled |
Uncheck to disable blocking (instead of removing the policy under Users&Groups > Users, Users&Groups > Groups, Computers or Application Control > General). |
Add Application Control Protocols |
Click to add one or multiple application protocols to the policy. |
Policy Assignment
System-wide Assignment
Important
- The system default application control policy allows HTTP, HTTPS and DNS traffic. Other traffic is blocked by default, e.g. access to social media. Adjust the policy to suit your needs.
- Ideally, system-wide and computer-level policies should block all applications. Access to applications and services should only be allowed after successful authentication.
- The system-wide policies apply to all traffic to and from the AXS Guard appliance, including VPN traffic. Traffic to and from the web-based administrator tool and SSH traffic are always allowed.
-
Go to Application Control > General.
-
Add the desired application control policies.
-
Update your configuration.
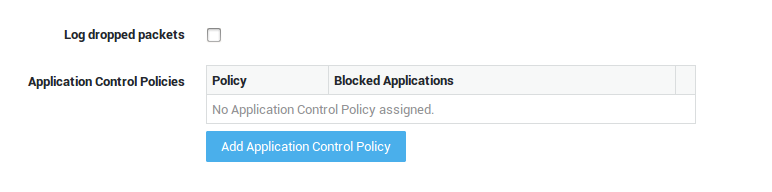
| Option | Description |
|---|---|
Log dropped packets |
Check to log all dropped traffic under Application Control > Logs and System > Logs > Network Security. |
Add Application Control Policy |
Click to add one or several application control policies at the system level. Go to Application Control > Policies for an overview of policies configured on your system. |
Computer-level Assignment
Important
Enforce user authentication where possible. Only allow applications that are absolutely necessary at the computer level.
-
Go to Computers.
-
Select the appropriate computer from the list.
-
Select the Application Control tab.
-
Select the appropriate option from the drop-down list (explained in the table below).
-
Save your configuration.
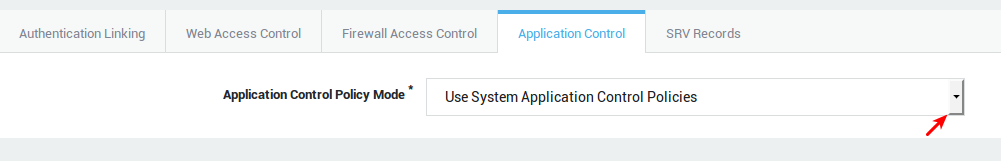
| Option | Description |
|---|---|
Use system application control policies |
Use the system-wide policies, assigned under Application Control > General. |
Add to system application control policies |
Assign specific policies to this computer, in addition to the system-wide policies configured under Application Control > General. |
Overrule system application control policies |
Do not enforce the system-wide policies, but only the specified policies. Specific policies are enforced based on the computer’s IP address. |
Group-level Assignment
Info
- Group-level policies are only enforced if a member of the group successfully authenticates.
- Separate policies can be configured to govern VPN traffic (remote access tab in the AXS GUARD group), e.g. to block selected applications accessed via a PPTP connection.
-
Go to Users & Groups > Groups.
-
Select the appropriate group from the list.
-
Select the Application Control tab.
-
Select the desired option from the drop-down list (explained in the table below).
-
Update your configuration.
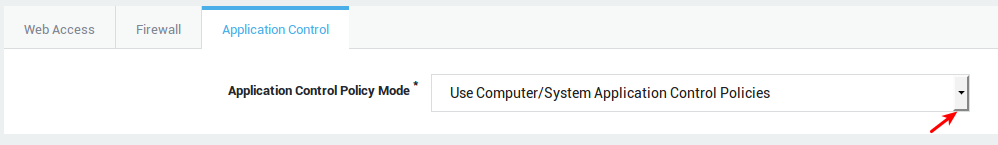
| Option | Description |
|---|---|
Use computer/system application control policies |
Enforce the system-wide policies, assigned under Application Control > General and the computer-level policies, if any. |
Add to computer/system application control policies |
Assign specific policies to this group, in addition to the system-wide policies configured under Application Control > General and computer-level policies, if any. |
Overrule computer/system application control policies |
Do not enforce the system-wide policies and computer-level policies, but only the specified policies. The specific policies will be enforced when a member of the group successfully authenticates. |
User-level Assignment
Important
- User-level policies are only enforced if the user successfully authenticates.
- Separate policies can be configured to govern VPN traffic (remote access tab in the AXS Guard user profile), e.g. to block selected applications accessed via a PPTP connection.
-
Go to Users & Groups > Users.
-
Select the appropriate user from the list.
-
Select the Application Control tab.
-
Select the appropriate option from the drop-down list.
-
Update your configuration.
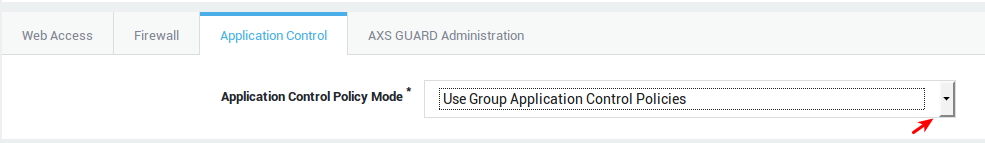
| Option | Description |
|---|---|
Use group application control policies |
Only enforce the policies as configured for the user’s group. |
Add to group application control policies |
Enforce the policies as configured for the user’s group and the policies that are specified in the user profile. |
Overrule group application control policies |
Only policies configured at the user, computer and system levels are enforced. Group policies are not enforced. |
Overrule Group / Computer / System Application Control Policies |
Only the application control policies configured at the user level are enforced. |
Proxy Server Application Control Policy
Important
Clients accessing the Internet via the AXS Guard proxy server are subject to the application control policy assigned under Web Access > Proxy Server. Computer, group-level and user-level application policies are not enforced in this case.
-
Go to Web Access > Proxy Server.
-
Select the application control policy or policies to be applied.
-
Update your configuration.
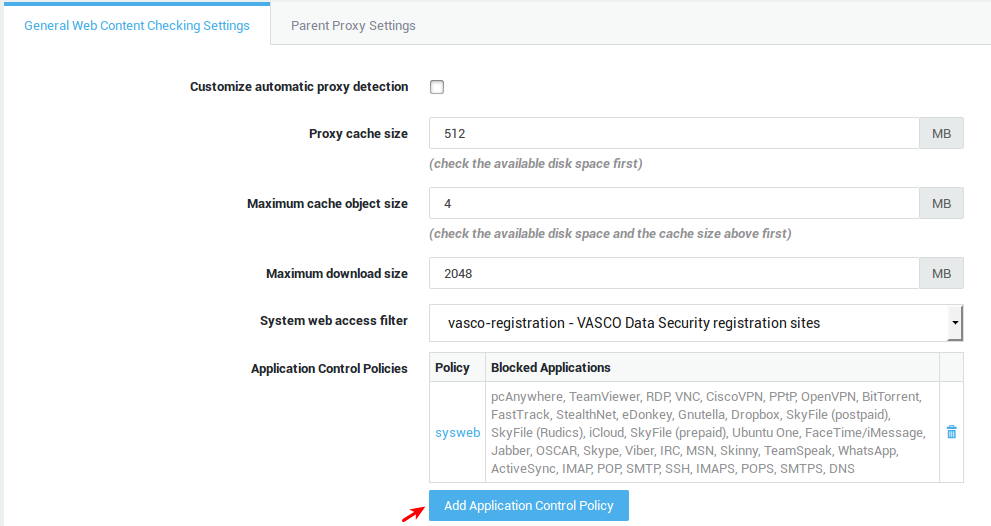
| Fields and buttons | Description |
|---|---|
Add application control policy |
Click to select and assign application control policies. Go to Application Control > Policies for an overview of policies on your system or to edit and configure application policies. |
Policy |
Shows the name of the assigned policy as defined under Application Control > Policies. |
Blocked applications |
A comma-separated list of applications which are blocked by the application control policy. |
VPN Application Control Policy
See the various VPN guides in the Product Manuals section of this site for additional information and configuration instructions.
Disabling Access Control
There are several methods to disable application control, i.e. to allow traffic otherwise blocked by an application control policy.
-
Go to Application Control > Policies and disable the appropriate policies.
-
By leaving the application control policies empty under Users & Groups, Computers or Web Access > Proxy Server (whichever applies).
-
By assigning an empty application control policy to a user, a group or the AXS Guard proxy.
Important
- Ideally, system-wide and computer-level policies should block all applications. Access to applications should only be allowed after successful authentication.
- The system-wide policies also affect traffic to and from the AXS Guard appliance, except traffic to and from the administrator tool and SSH traffic, which are always allowed.
Logging, Statistics and Connection Tracking
Overview
In this section, we explain how to access the following information:
-
Application Control Logs: Information about traffic dropped by the application control system, e.g. blocked connections to Facebook.
-
Application Control Statistics: Graphical representation of all connection data.
-
Network Security Logs: A compilation of information related to traffic dropped by the AXS Guard firewall, the IPS, GeoIP filtering, SecureDNS and the application control system.
-
Connection Tracking: Information about active connections, such as the source and destination IP addresses, port number pairs, etc.
Application Control Logs
-
Go to Application Control.
-
Select
Logs. -
Click on the desired log file (date) to open it.
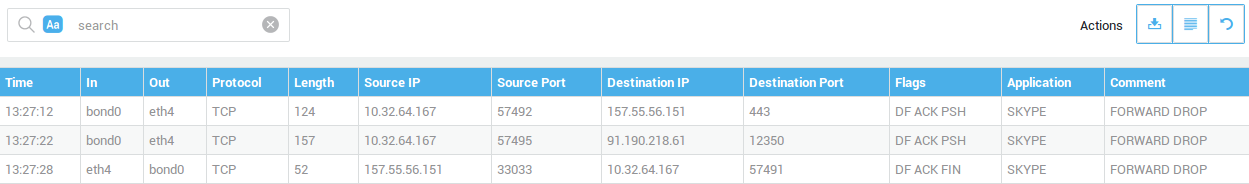
| Field | Description |
|---|---|
Time |
The time the event was recorded. |
In |
The network device that handles incoming traffic for a given connection. |
Out |
The network device that handles outgoing traffic for a given connection. |
Protocol |
The protocol used by the application, e.g. TCP, UDP. |
Source IP |
The IP address, associated country or hostname of the source host. Hover over the flag icon to see the source IP address. |
Destination IP |
The IP address, associated country or hostname of the destination host. Hover over the flag icon to see the destination IP address. |
Destination Domain |
Domains that were requested by the device that initiated the connection (Source IP). |
Source Port |
The source port used by the host which initiated the connection or by the replying host. |
Destination Port |
The destination port used by the host which initiated the connection or by the replying host. |
Flags |
Detected TCP flags. |
Application |
The name of the application that was matched. |
Comment |
The action taken by the application control engine, e.g.
|
Statistics and Reporting
-
Go to Statistics
-
Click on
Application Control.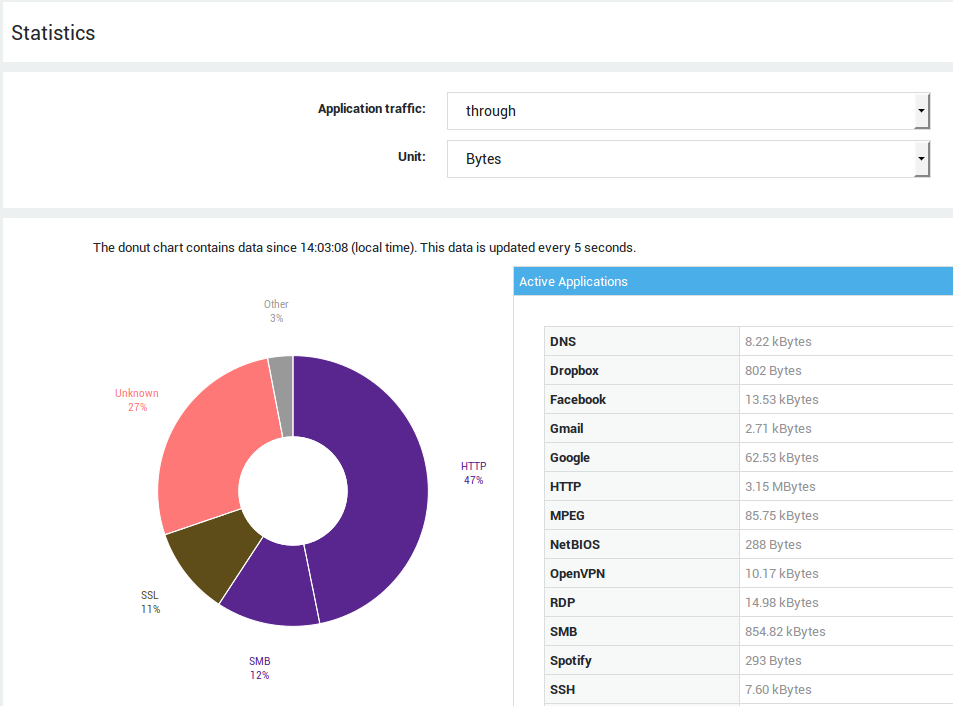
Option |
Description |
|---|---|
Application Traffic |
|
Unit |
The unit to be displayed in the application control statistics, i.e. bytes or packets. |
Time interval |
Select the appropriate time interval from the drop-down list. |
Current Classification
Donut Chart
When the page is initially rendered, the donut chart is populated with data generated since the time the firewall was first started or the application control feature was activated. After 5 seconds, the donut chart will be automatically refreshed and only show current data. This will provide administrators with a live view of traffic passing through the appliance.
Detailed table view
This table contains the raw data shown in the donut chart. The first 5 seconds it will contain statistics that have been collected since the time the firewall was started or the application control feature was activated. After 5 seconds, the table will be refreshed and only show current statistics.
Historical Classification
The line chart allows you to view the evolution of the application use over an extended period. The view consists of a detailed graph and an overview graph. You can change the range of the detailed view by using the selectors or selecting an area in the graph. The range of the overview graph is controllable by pressing the buttons below the chart.
By default, only unrecognized traffic is shown. This default behavior can be changed by checking the appropriate checkboxes in the table under the graph.
Network Security Logs
The network security logs are a compilation of information related to traffic dropped by the AXS Guard firewall, the IPS, SecureDNS, GeoIP filtering and the application control system.
-
Go to System > Logs > Network Security.
-
Click on the desired log file to open it.
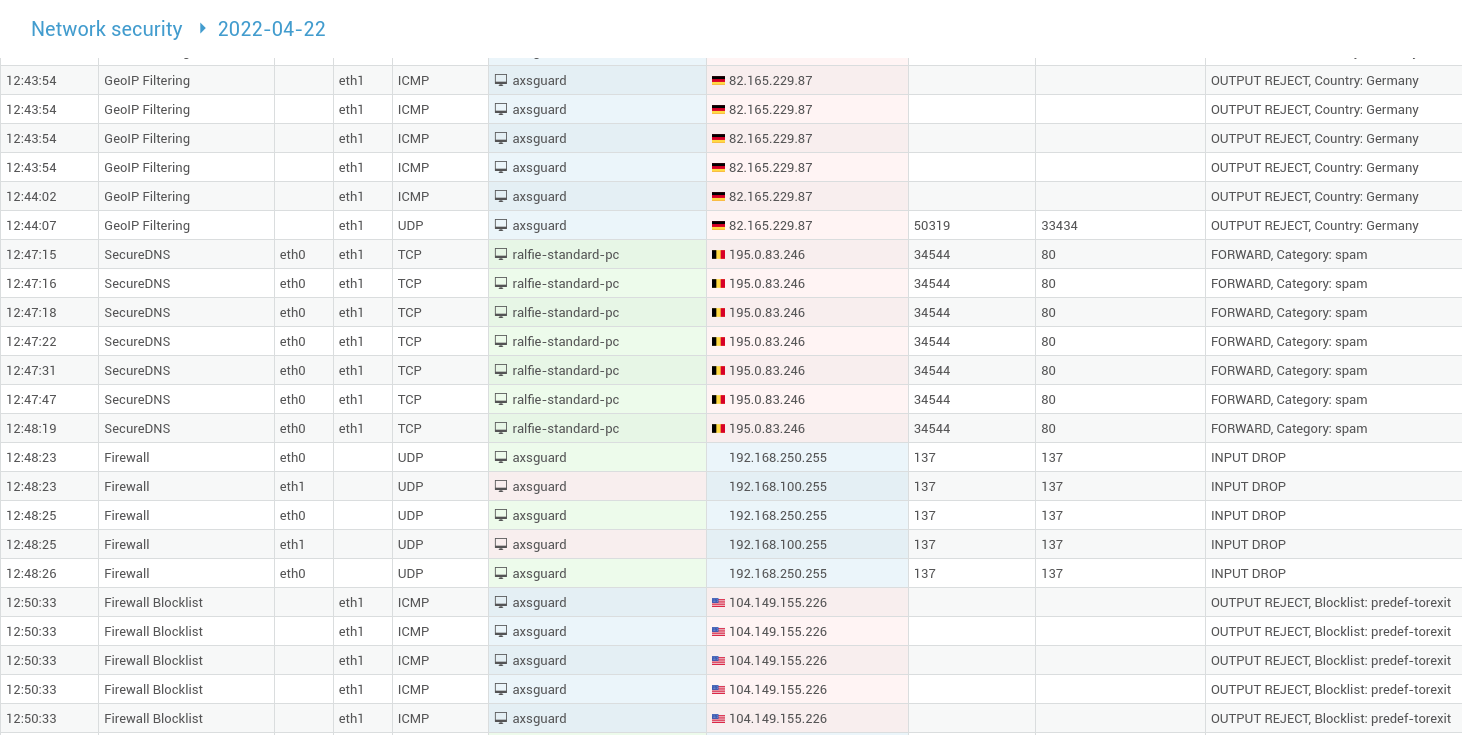
| Field | Description |
|---|---|
Time |
The time at which the log entry was created. |
Triggered by |
The process that blocked the network traffic. |
In |
The network device on the receiving end of the connection. |
Out |
The forwarding network device. |
Source IP |
The IP of the sending host. |
Source Port |
The source port used by the sending host. |
Destination IP |
The IP of the receiving host. |
Destination Port |
The destination port on the receiving host. |
Comment |
The action taken by the application in the |
Connection Tracking
Flow Viewer
The flow viewer allows you to consult active connections and use filters to extract information based on the:
-
Protocol
-
Source IP and port
-
Destination IP and port
-
Network device
-
Connections that are monitored by the application control system
Viewing Active Connections
-
Go to Network > Tools.
-
Select
Flow Viewer.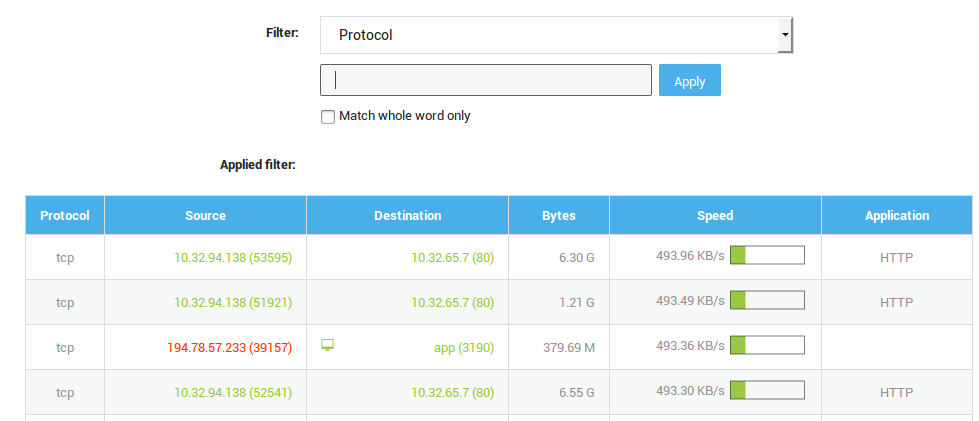
-
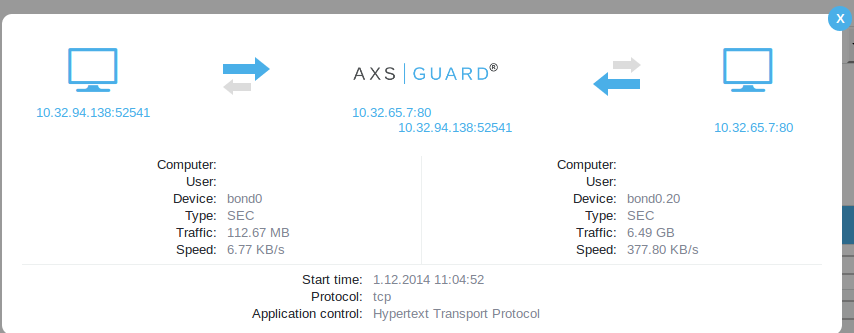
Click on an empty space in a row to view details about a connection.
Support
If you encounter a problem
If you encounter a problem with AXS Guard, follow the steps below:
-
Check the troubleshooting section of the feature-specific manual.
-
Check the knowledge base on this site for information about special configurations.
-
If no solution is available in any of the above sources, contact your AXS Guard vendor.
Contact Information
(+32) 15-504-400
support@axsguard.com
