How to configure a DMZ
Introduction
About this Document
In this document we explain various use cases regarding demilitarized zones (DMZ). Some of the concepts presented in this document are also explained in the Firewall Zones KB article. This document was last updated on 16 Sep 2019.
What is a DMZ?
A DMZ is a neutral network zone where public and private services meet. This zone is directly accessible from the Internet, but strictly separated from the secure zone . It is typically used to host public services, such as web servers and SMTP servers. Hosts in a DMZ can either have public or private IP addresses. As hosts in a DMZ are directly accessible from the Internet, they are easier to attack and more susceptible to remote exploits. This is why it’s critical to allow absolutely no or very restricted network access from the DMZ to your LAN using the firewall. That way, even if a DMZ host is breached, attackers can’t get into your LAN.
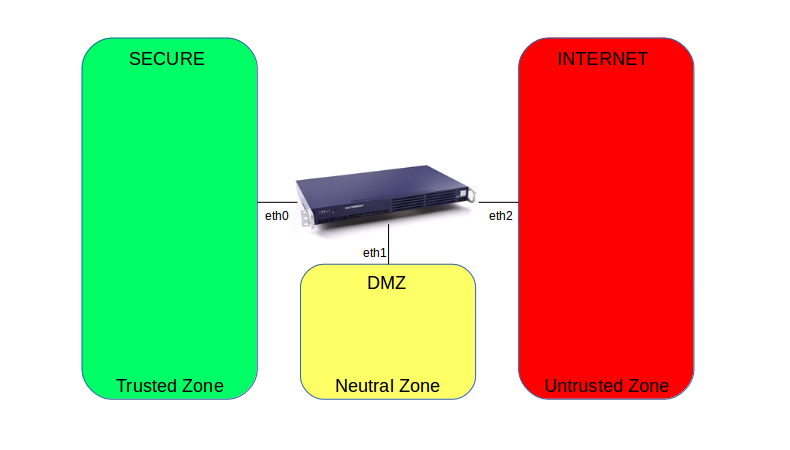
When should I use a DMZ?
Typical use of a DMZ includes, but is not limited to, a public website, a corporate extranet or a mail server. Such systems need to be easily accessible from the Internet and possibly from your LAN as well. In any case, these DMZ systems should not be able to access your LAN.
When not to use a DMZ
Do not use a DMZ when your goal is to split your internal network into multiple segments. A typical misconfiguration is setting up separate WiFi segments for employees and visitors. This is not the intended purpose of a DMZ and will most likely unnecessarily complicate things in the future. Especially if you consider that employees need access to hosts and services in the secure LAN.
Setting up a DMZ with a public IP address
Why should I use a public IP address?
When systems in your DMZ have their own public IP addresses, they can communicate directly to the outside world; no special NAT rules or masquerading are required. If an attack is executed on a DMZ host with its own public IP address, only that specific system, which is still protected by the AXS Guard firewall and IPS, is affected.
Subnet Requirements
You need at least a single /29 or two /30 subnet ranges from your ISP. A /29 subnet will be split into two /30 subnets, allowing 2 hosts for each /30 subnet. This translates to one IP address for the appliance’s Internet interface, one for the DMZ interface and only one IP address for a DMZ host. If you need multiple Internet IP addresses and/or multiple public IP addresses for your DMZ, at least a single /28 subnet or two /29 subnets will be required.
Why do I need a single /29 or two /30 subnets?
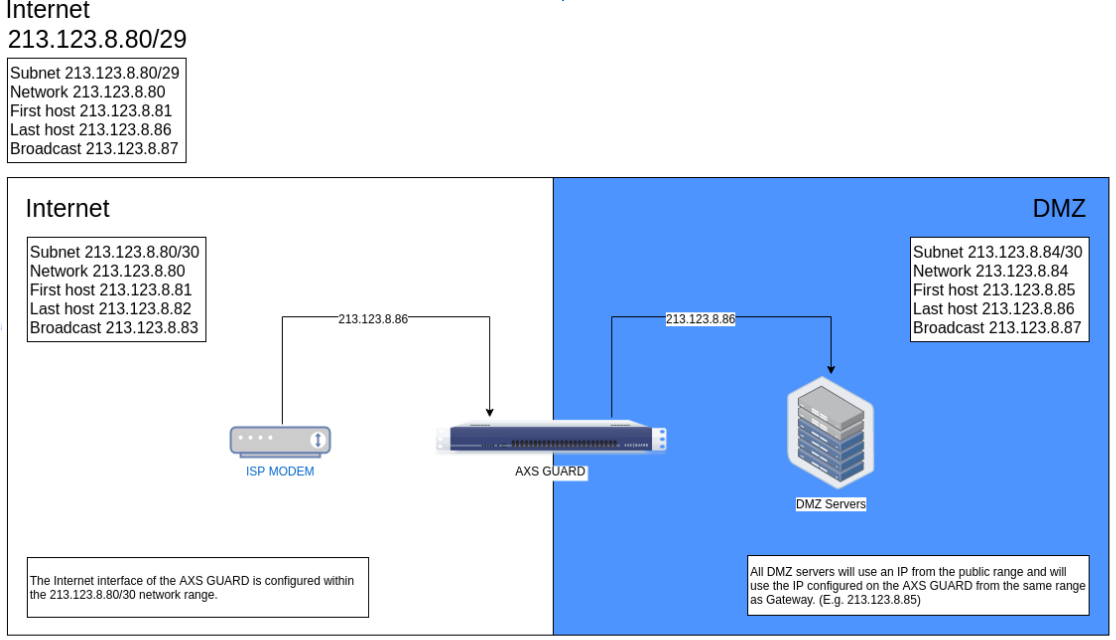
Example: DMZ Subnets
You are assigned the following subnet 213.123.8.80/29 by your ISP.
-
Network IP = 213.123.8.80
-
First available host IP = 213.123.8.81
-
Last available host IP = 213.123.8.86, giving you 6 available host IP addresses
-
Broadcast IP = 213.123.8.87
But you can’t use the same subnet on your Internet interface and DMZ interface, so you need to split the subnet into two smaller subnets.
Subnet 1
-
Subnet 1 = 213.123.8.80/30
-
Network IP = 213.123.8.80
-
First available host IP = 212.123.8.81 = ISP modem/router/gateway
-
Last available host IP = 212.123.8.82 = AXS Guard INT interface
-
Broadcast IP = 212.123.8.83
Subnet 2
-
Subnet 2 = 213.123.8.84/30
-
Network IP = 213.123.8.84
-
First available host IP = 213.123.8.85 = AXS Guard DMZ interface
-
Last available host IP = 213.123.8.86 = DMZ server
-
Broadcast IP = 213.123.8.87
So with only one /29 or two /30 subnets, you can only have 4 host IP addresses, of which two are needed for AXS Guard, one is used for the ISP and one is used for a single DMZ server.
If you have more public IP addresses than the required minimum, you can assign more IP addresses to DMZ systems, but then you need to make sure you have at least 3 available host IPs for your DMZ, which means you need at least a /29 subnet for your DMZ.
Schematic Diagram
AXS Guard Configuration
Internet Interface
-
Determine the IP address of the gateway to be used by AXS Guard (ISP router/modem/gateway). Mark this IP address as IP_X in subnet 1.
-
Configure the internet interface with IP address IP_Y in subnet 1 and IP_X as default gateway.
DMZ Interface
-
Configure the DMZ interface with IP address IP_A in subnet 2.
-
Configure the DMZ server with IP address IP_B in subnet 2 with IP_A as the default gateway.
-
If you have a second DMZ server, configure it with IP address IP_C in subnet 2 with IP_A as the default gateway.
Firewall Configuration
Create the required firewall rules in Firewall > Rules > DMZ
Filter to allow access to the required ports and/or IP addresses in the
DMZ. The more restricted, the better. So we highly recommend you use
destination IP addresses and destination ports in the dmzf-rules. Add
the newly created rules to the static stat-dmz-filter firewall policy.
If your DMZ server needs to be able to connect to the internet, create the required firewall rules in Firewall > Rules > Through and add them to a static firewall policy or dynamic firewall policy that is assigned to the AXS Guard computer entry created for that server. Dynamic firewall policies are preferred.
Setting up a DMZ with private IP addresses
When should I use private IP addresses in my DMZ?
If you don’t have a /29 or two /30 public IP subnets at your disposal, then you need to configure your DMZ with private IP addresses. This is also an option is you simply don’t want to use public IP addresses for your DMZ or because you prefer to use masquerading (NAT).
Important
In this scenario, all DMZ servers share the same public IP address, which means you cannot use round robin DNS for load balancing.
Requirements
Reserve a subnet for your DMZ in a range that is not used elsewhere in your network, including VPN tunnels. Undesirable routing conflicts will occur otherwise.
Schematic Diagram
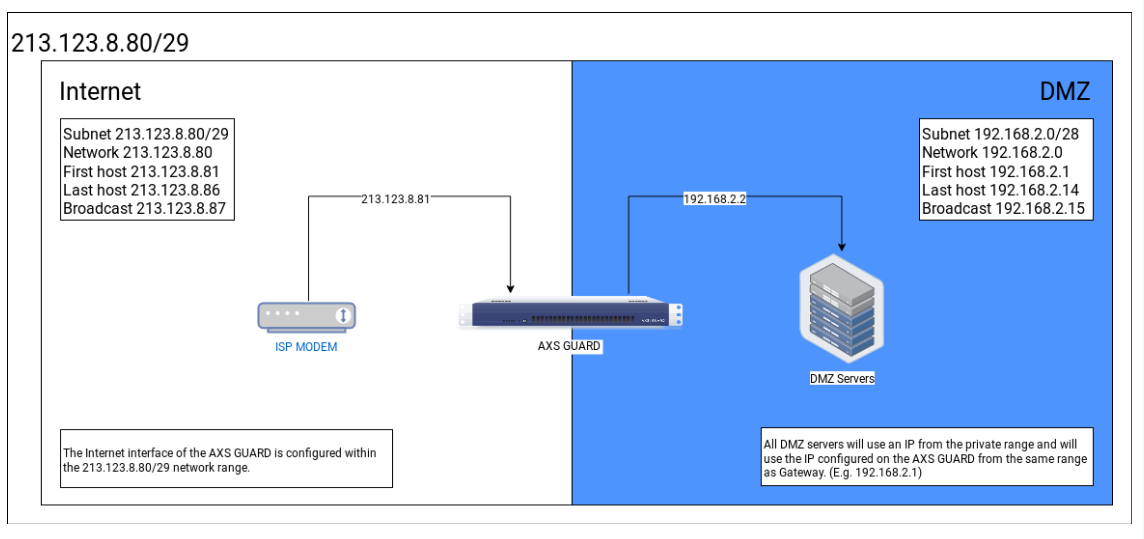
AXS Guard Configuration
Internet Interface
No specific configuration required.
DMZ Interface
Configure the DMZ interface with an IP address in a private IP range, i.e. 10.0.0.0 - 10.255.255.255, 172.16.0.0 - 172.31.255.255 or 192.168.0.0 - 192.168.255.255.
NAT Rules
-
Go to Network > NAT > Masquerading to create a MASQ rule to masquerade traffic originating from the DMZ going towards the Internet. Failing to do so will cause traffic to be dropped when it leaves the AXS Guard appliance, as private IP addresses don’t work on the public Internet.
-
Create the required port forwarding rules via Network > NAT > Port Forwarding to forward traffic from the Internet to the DMZ server. You can select only one destination IP address; so no load balancing is possible here. If you need load balancing, it must be set up separately between the AXS Guard appliance and the DMZ servers.
Firewall Configuration
If your DMZ server needs to connect to the Internet, go to Firewall > Rules > Through and add the rules to a static firewall policy or a dynamic firewall policy that is assigned to the AXS Guard computer entry created for the DMZ server. Dynamic firewall policies are preferred.