Firewall Zones¶
Introduction¶
About this Document¶
In this document we explain the various AXS Guard network zones, the default firewall behavior which applies to traffic between these zones and special cases where advanced firewall rules are required to bypass the default behavior of the AXS Guard firewall.
About the AXS Guard Firewall¶
The AXS Guard firewall is based on iptables. Detailed information about iptables is beyond the scope of this document. See the appropriate online references for tutorials and additional information.
Knowlegde of iptables is only required to configure advanced firewall rules on the system. Most rules and policies can be configured via the web-based administrator tool of the AXS Guard appliance. See the AXS Guard firewall manual for instructions.
Network Zones¶
Introduction¶
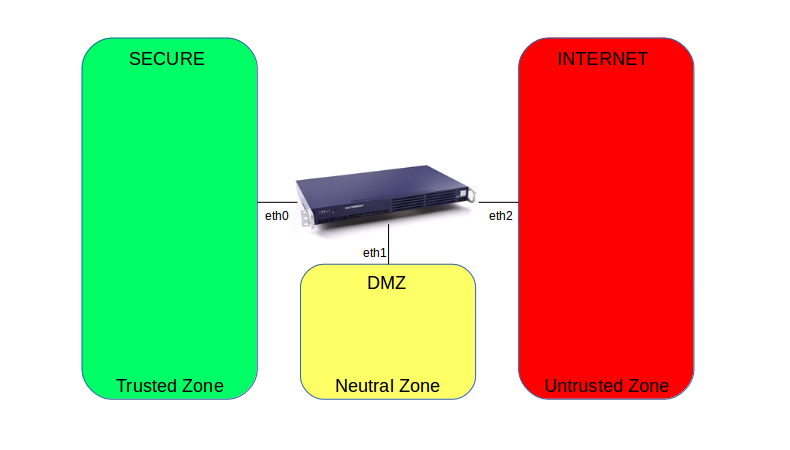
A network zone can be defined as a physical network to which the AXS
Guard appliance is connected. There are 3 distinct network zones: the
secure zone, the Internet zone and the DMZ. Each zone can consist of
multiple networks, e.g. you can have more than 1 secure LAN or DMZ. Each
zone is connected to the AXS Guard appliance via a dedicated network
(eth) device.
| Network Zone | Description |
|---|---|
Secure Zone (SEC) |
The combination of all secure LAN and Virtual Private Network devices, e.g. IPsec, PPTP and OpenVPN devices. Hosts that are connected to the AXS GUARD appliance via a VPN connection are considered part of the secure zone. Devices in the secure zone have private IP addresses as defined in RFC 1918. |
Internet Zone (INT) |
All network devices that are connected to the Internet. Devices in the Internet zone have public IP addresses in most cases, except in NAT setups where private IPs are used. |
Demilitarized Zone (DMZ) |
Neutral zone where public and private services meet. This zone is directly accessible from the Internet, but strictly separated from the secure zone . It is typically used to host public services, such as web servers and SMTP servers. Devices in the DMZ can either have public or private IPs. |
Default Firewall Behavior¶
By default, the following zone (network device) combinations are not allowed by the AXS Guard firewall because they are inherently insecure. To bypass this behavior, advanced firewall rules must be used.
-
Internet to secure zone
-
Internet to Internet
-
DMZ to secure zone
From / To |
to SEC |
to DMZ |
to INT |
From SEC |
allowed |
allowed |
allowed |
From DMZ |
advanced firewall rules |
allowed |
allowed |
From INT |
advanced firewall rules |
allowed (dmzf) |
advanced firewall rules |
Important
VPN tunnel devices, such as IPsec, PPTP and OpenVPN devices are part of the secure (SEC) zone.
Network Address Translation¶
While network packets travel from a source address to a destination address, routers such as the AXS Guard appliance which use NAT (Network Address Translation), alter the source and destination headers of the IP packets. In case of UDP and TCP, the source and destination ports can also be altered.
The different NAT types are explained in the AXS Guard system administrator guide.
Default NAT Actions¶
The AXS Guard applies pre-defined masquerading in the following order by default:
| In Interface | Out Interface | Masquerading applied? |
|---|---|---|
DMZ |
Internet |
No |
Secure LAN |
DMZ |
Yes |
Secure LAN |
Internet |
Yes |
Predefined Masquerading Rules
If none of the above combinations match, the packet is either:
-
not masqueraded
-
blocked by the firewall
| From | To | Action |
|---|---|---|
LAN |
LAN |
ACCEPT |
LAN |
DMZ |
MASQ |
LAN |
Internet |
MASQ |
DMZ |
LAN |
DROP |
DMZ |
DMZ |
ACCEPT |
DMZ |
Internet |
ACCEPT only if DMZ has public IP |
Internet |
LAN |
DROP |
Internet |
DMZ |
ACCEPT |
Internet |
Internet |
DROP |
Important
In some situations, the predefined masquerading rules do not suffice. Traffic towards the Internet originating from hosts with private IP addresses in the DMZ will be discarded if no masquerading is applied, because private IPs are reserved for hosts in private networks and are considered "non-routable".
In such cases, specific masquerade rules must be configured to allow traffic originating from these hosts to be routed over the Internet. See the system administrator manual for instructions.
Firewall Troubleshooting¶
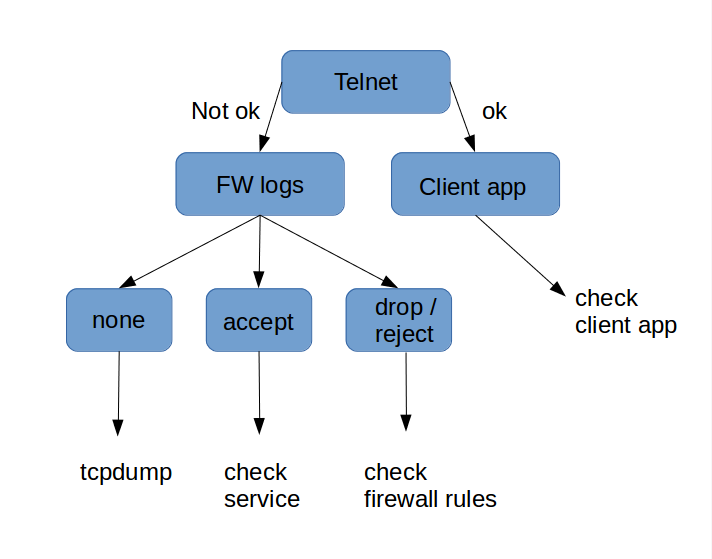
Important
The IPS may still be blocking traffic allowed by the firewall. Check and update your IPS configuration if necessary.