OpenVPN Access Server¶
Introduction¶
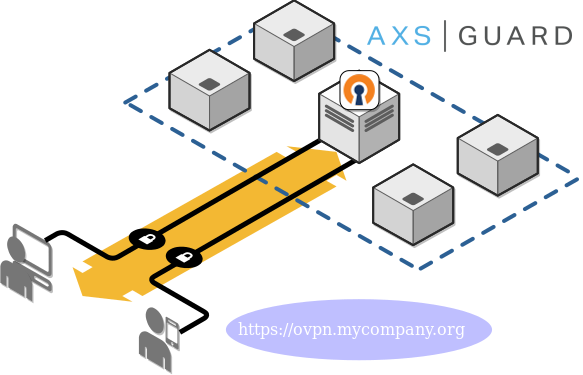
This document provides instructions for configuring a custom URL for users to connect to the AXS Guard OpenVPN Access Server using the OpenVPN Connect app. The custom URL replaces the static URL provided by AXS Guard Cloud. This document is intended for system administrators and IT professionals.
Requirements¶
Public DNS Records¶
To allow users to connect to your OpenVPN Access Server using a custom domain name, create a public DNS record (A record) that points to the server's public IP address. Refer to your DNS provider's documentation for specific instructions on creating an A record.
Server Certificates¶
Server certificates are required for the OpenVPN AS and the OpenVPN server.
| Server Type | Requirements |
|---|---|
| OpenVPN AS | A valid certificate signed by a public Certificate Authority (CA) is required for the domain name associated with the public DNS record. The OpenVPN Connect app does not accept self-signed certificates or certificates signed by an untrusted CA by default. The certificate must be imported via PKI > Certificates on your AXS Guard appliance before you can assign it to the OpenVPN AS. |
| OpenVPN Server | Use the AXS Guard built-in CA to issue the server certificate and assign it to the OpenVPN server. |
Client Certificates¶
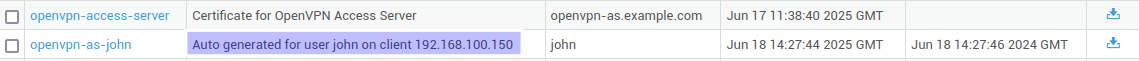
To establish a VPN connection, users need a valid client certificate. AXS Guard automatically issues these client certificates to users upon successful connection to the OpenVPN access server, as shown in the example below. Go to PKI > Certificates for an overview of certificates issued by AXS Guard.
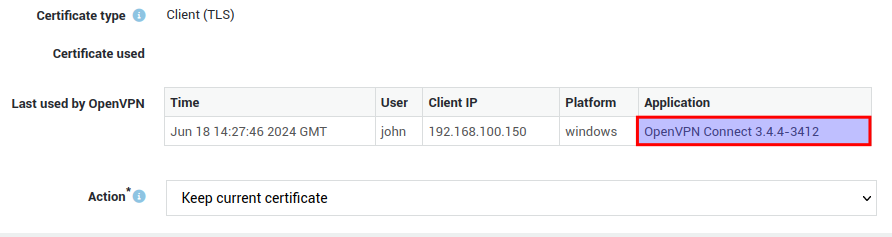
Click on the certificate name in the overview to view additional details:
Server-side Configuration¶
Refer to the AXS Guard OpenVPN server documentation for detailed configuration instructions. This document focuses solely on the OpenVPN network configuration and local access server settings required for this specific setup. For proper operation, the AXS Guard appliance needs to be reachable over the internet via TCP port 443. Firewall rules are created automatically upon saving your configuration.
Network Settings¶
- Log in to your AXS Guard appliance.
- Navigate to VPN > OpenVPN > Server.
-
Configure the network settings as shown in the example below (change the default protocol and server port).
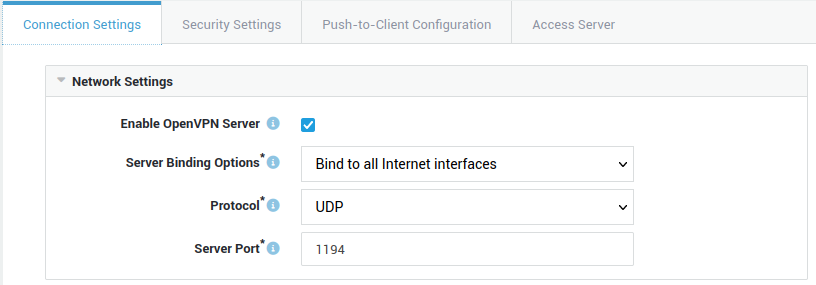
Access Server Settings¶
- Select the Access Server tab.
-
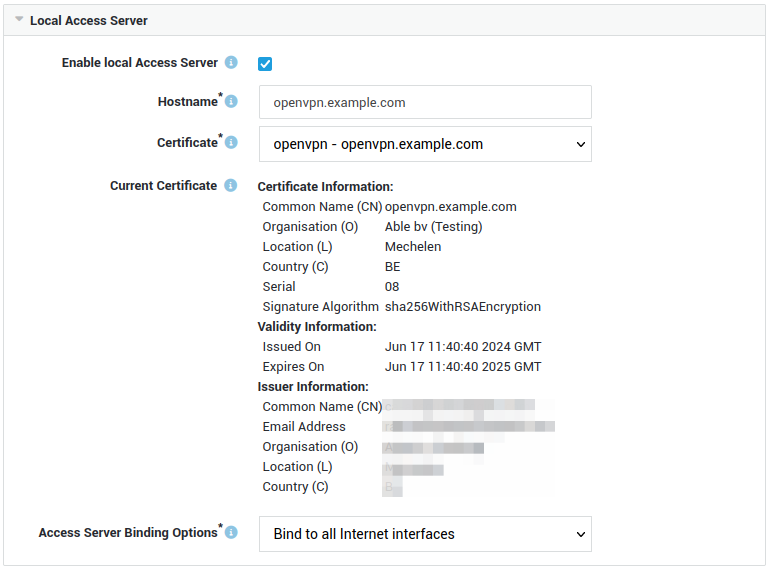
Configure the local access server settings as shown in the example below.
- Assign the certificate associated with the public DNS record of the OpenVPN AS.
- The hostname must match the name as configured in your public DNS record(s) as well as the CN (or one of the Subject Alternative Names) in the server certificate.
User Authentication¶
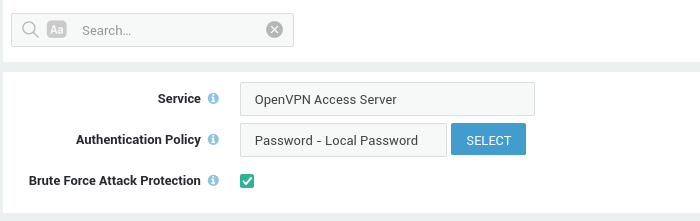
Ensure that the appropriate users are granted access to OpenVPN. Configure the authentication policy for the OpenVPN AS, as explained in the OpenVPN server documentation.
Testing your Connection¶
Follow the connection instructions as provided in the OpenVPN server documentation.
Logs¶
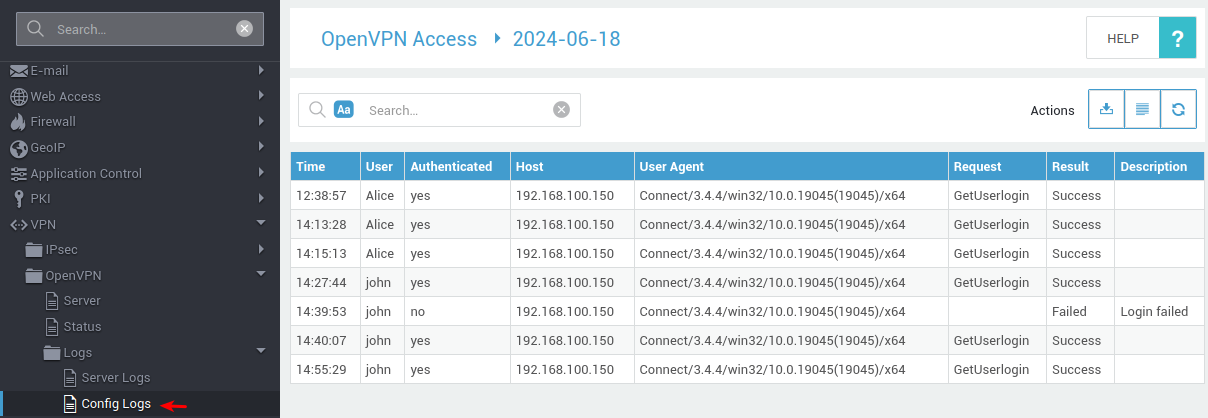
Two types of server-side logs exist for the OpenVPN Connect app: Config and Access Server.
OpenVPN Config Logs¶
- Log in to your AXS Guard appliance.
- Navigate to VPN > OpenVPN > Logs > Config Logs.
-
Select the appropriate date.
Access Server Logs¶
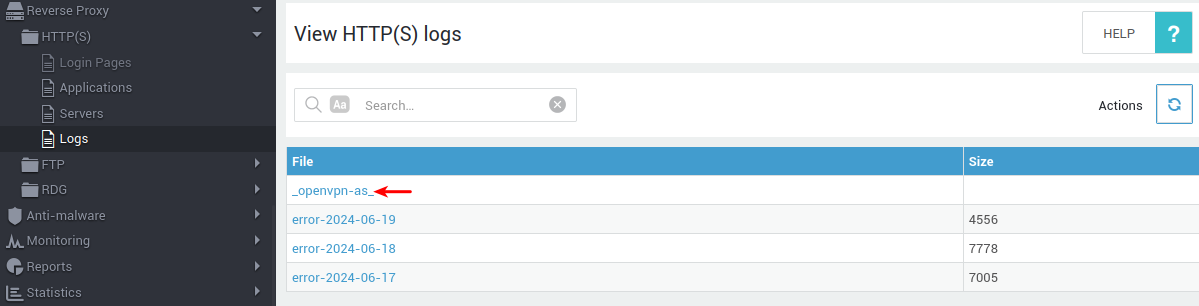
- Log in to your AXS Guard appliance.
- Navigate to Reverse Proxy > HTTP(S) > Logs.
-
Select
_openvpn-as_, thenrewrite,errororaccess.