SSO for OpenVPN Access Server with Microsoft Entra ID¶
Introduction¶
This guide explains how to set up SSO with Microsoft Entra ID (Azure Active Directory) for users connecting to the AXS Guard OpenVPN Access Server via the OpenVPN Connect app. AXS Guard leverages OpenID Connect, a library that enables applications to authenticate users via OAuth 2.0, a modern industry-standard protocol.
Requirements¶
- Windows clients must be Microsoft Entra joined or capable of browser-based Entra ID authentication using Microsoft Edge or Google Chrome.
- The use of Conditional Access Policies in Microsoft Entra ID (formerly Azure AD) requires specific licenses.
- User synchronization and authentication with Microsoft Entra ID must be successfully configured in AXS Guard.
- Users must have an OATH token (e.g., Microsoft or Google Authenticator) assigned.
- A fully configured and operational AXS Guard OpenVPN Access Server ({ title="Only use the AXS Guard Cloud URL, e.g. https://0000-00012345.appliances.axsguard.cloud/" } excluding Local Access Server configurations; custom URLs are not supported).
- A Microsoft Entra ID account with sufficient permissions to register apps.
- The application secret, application ID and redirect URI (OAuth 2.0) must be correctly configured.
Documentation¶
Before proceeding with this guide, please ensure you have reviewed the following documentation:
| Document Title | Description |
|---|---|
| AXS Guard OpenVPN Guide | Understand the basic configuration and operation of the AXS Guard OpenVPN Access Server. |
| AXS Guard Directory Services | Understand the basic configuration and operation of AXS Guard Directory Services, including user management, server settings, and Microsoft Entra ID user synchronization. |
| Microsoft Entra ID Documentation | Familiarize yourself with the core concepts of Microsoft Entra ID (formerly known as Azure Active Directory), including user management, application registration, and authentication flows. |
Entra ID App Registration¶
Redirect URI¶
- Log in to https://entra.microsoft.com/ as a tenant admin.
-
Go to Applications > App registrations in the Entra admin center and click new registration.
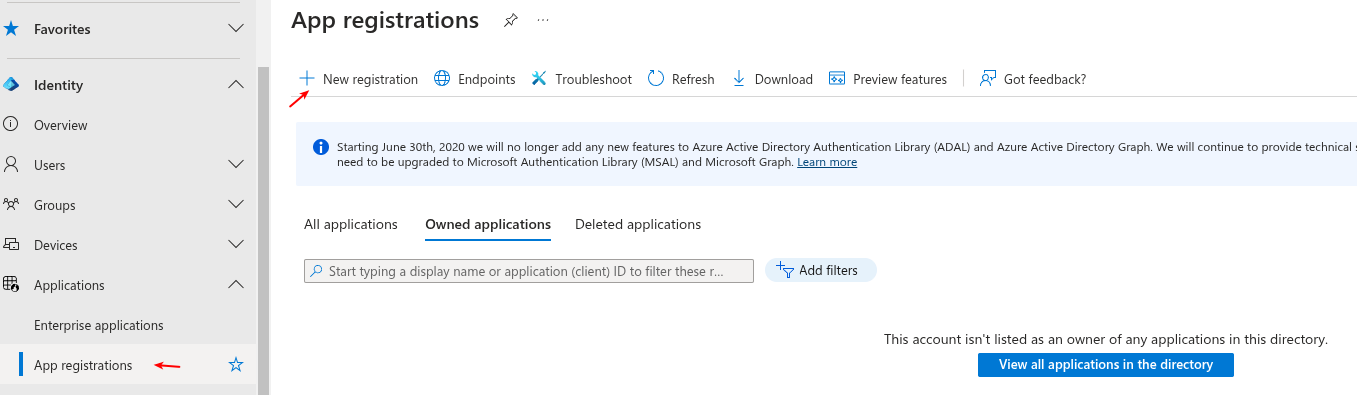
-
Pick a user-facing display name, select a supported account types option. Leave the default value, if you are unsure.
-
Under Redirect URI, select Web and enter the redirect URI, for example:
https://0000-00012345.appliances.axsguard.cloud/oidc/callback- Replace
0000-00012345with the license number of your AXS Guard appliance.
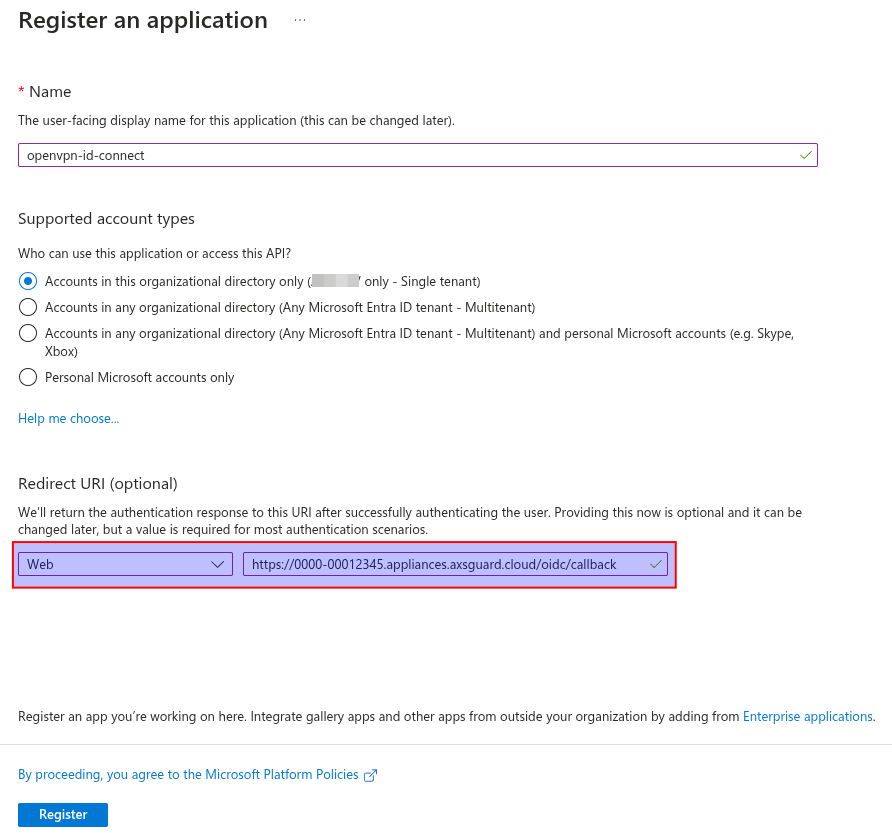
-
Click register.
Client Secret & App ID¶
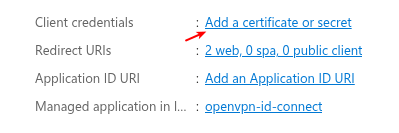
- Go to Applications > App registrations and select All applications, then search for the application you just created and select it.
-
Click on add a certificate or secret.
-
Click on new client secret, enter a description, select the desired lifespan, then click on add.
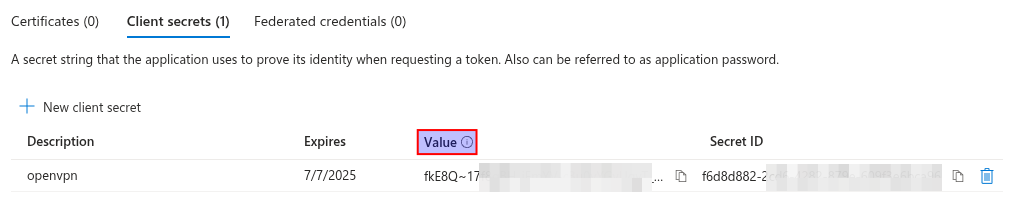
-
Copy the client secret (value) you just created. You will need this to further configure AXS Guard.
- Go to Applications > App registrations and select All applications, then search for the application you just created and select it.
-
Copy the client application ID. You will need this to further configure AXS Guard.

Token Configuration¶
-
Select Token configuration on the left side and click on add optional claim.
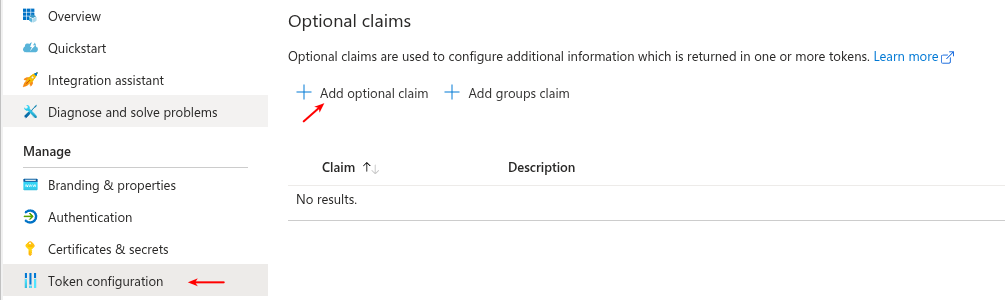
-
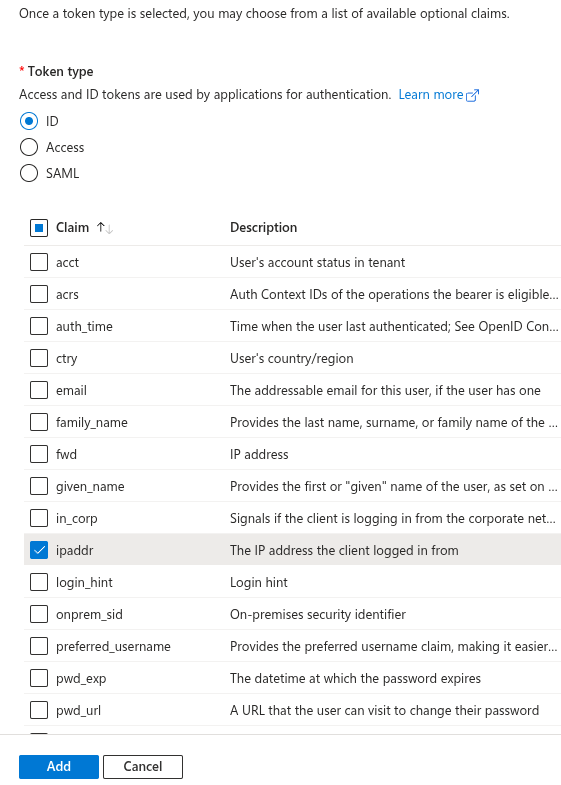
On the right panel, select ID as token type.
-
Select ipaddr from the list of claims and then click add.
OpenVPN Server Configuration¶
Security Settings¶
- Log in to your AXS Guard appliance.
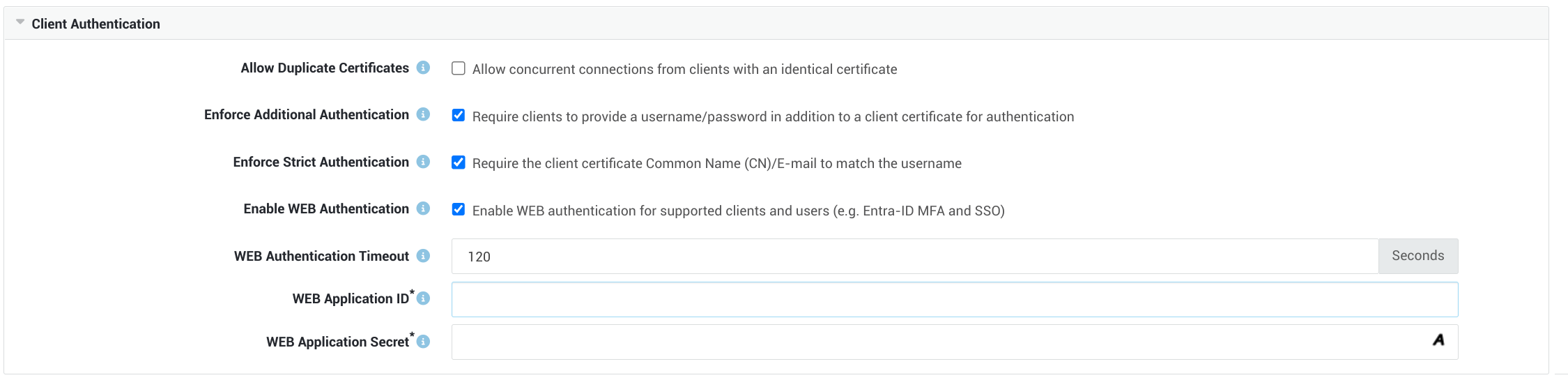
- Go to VPN > OpenVPN > Server and select the Security Settings tab.
- Enable WEB Authentication, then enter the application secret and application ID (see steps 4 and 6 in the Client Secret & App ID section).
-
Update your configuration.
Authentication Policies¶
- Log in to your AXS Guard appliance.
- Go to Authentication > Services.
- Ensure the authentication policy for the OpenVPN Access Server is set to
DirectoryService(Microsoft Entra ID). -
Ensure the authentication policy for OpenVPN is set to
OATH.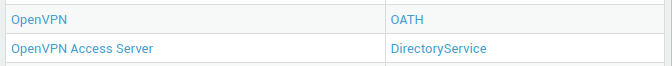
Testing your VPN Connection¶
In this scenario, the Windows client is already joined to Microsoft Entra ID (Azure AD). Joined devices provide users with a seamless single sign-on (SSO) experience to your tenant's cloud applications.
To connect to the AXS Guard OpenVPN server using Entra ID-joined SSO:
- Log in to the Windows workstation: Use your Entra ID credentials to log in.
- Launch the OpenVPN Connect app: Open the OpenVPN Connect application on your workstation. { title="Only use the AXS Guard Cloud URL, e.g. https://0000-00012345.appliances.axsguard.cloud/" }
- Connect to the server: Click the slider button within the OpenVPN Connect app to initiate the connection to the AXS Guard OpenVPN server.
- Browser notification: A notification will appear in your Microsoft Edge or Google Chrome browser indicating that access has been granted.
- Close the browser window: You are now connected to the corporate network.