Terminal Servers¶
Introduction¶
About this Document¶
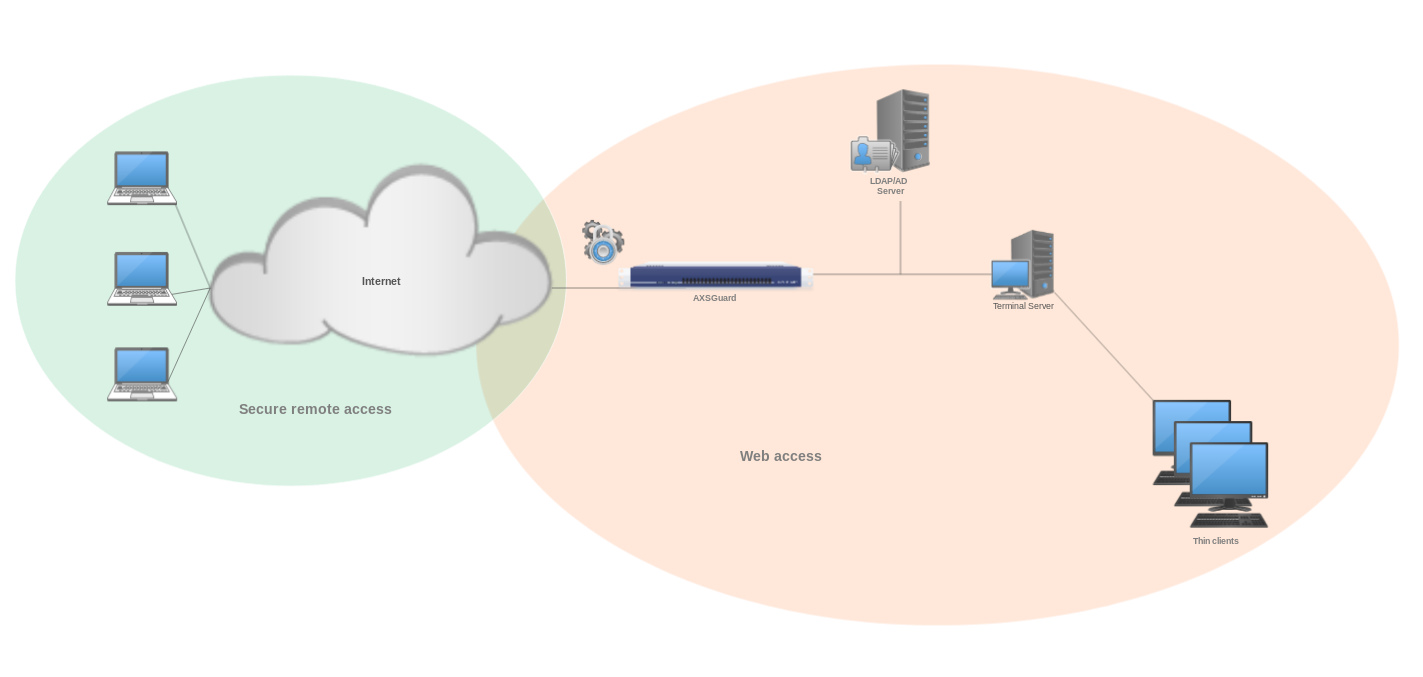
The objective of this article is to provide an overview of the most common configurations related to authentication and access to terminal servers.
Related Documentation¶
For additional information about the concepts presented in this document, refer to the following feature manuals on this site:
-
SSO Tool Setup Manual
-
Authentication Manual
-
Reverse Proxy Manual
Info
Also see the context-sensitive help on the AXS Guard appliance.
Terminal Server Setups¶
Web Access Authentication¶
About¶
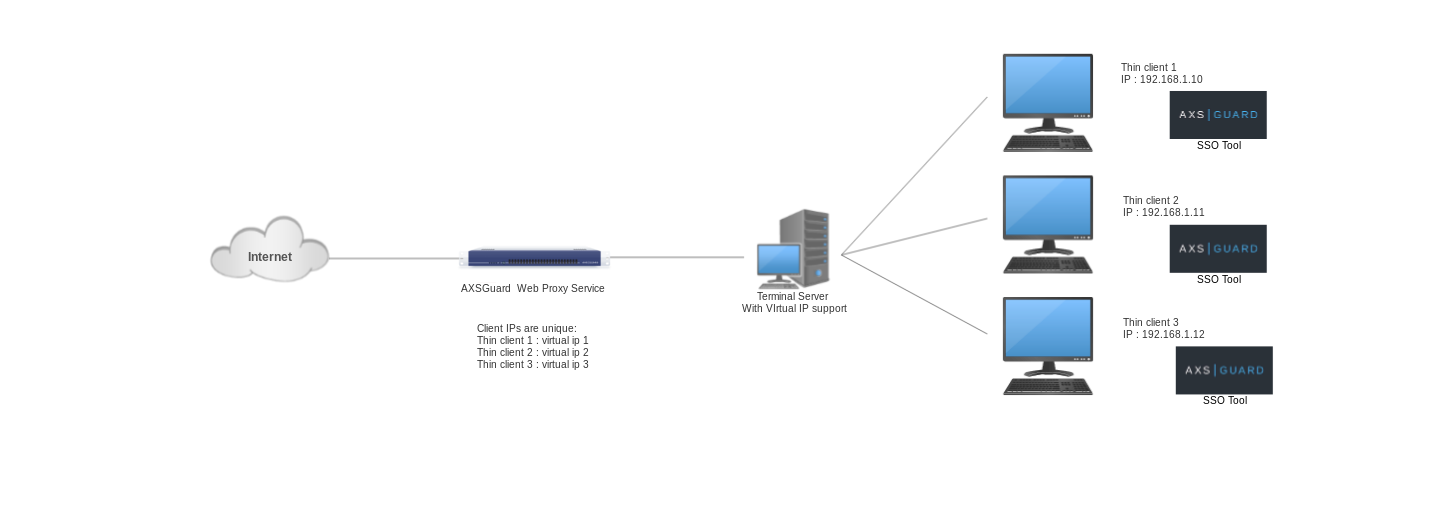
If your terminal server supports virtual IP addresses, i.e. one IP per terminal client, you can use the SSO tool. If this is not the case, you should choose another user authentication mechanism, such as Kerberos authentication.
SSO with Virtual IP¶
See the SSO Tool manual for additional details and configuration instructions.
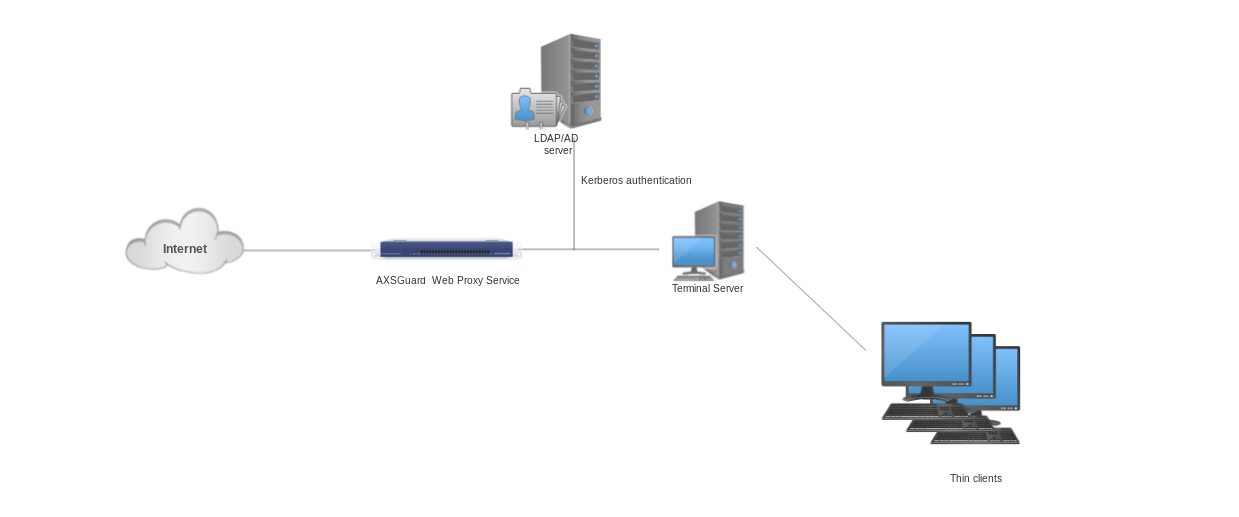
Kerberos¶
See the Authentication manual for additional details and configuration instructions.
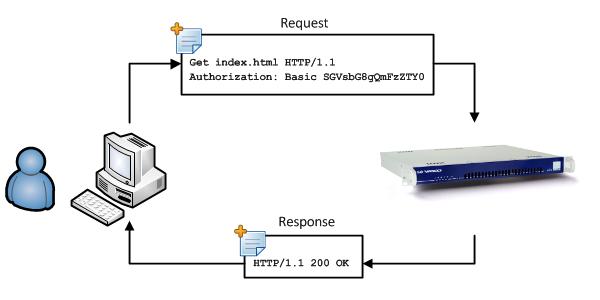
Basic Authentication¶
Another option is to make use of basic authentication as defined in RFC 7617. With basic authentication, users will be prompted to enter their credentials in a browser popup window before they are allowed to access the Internet. This setup is less common due its obvious restrictions.
See the Authentication manual for additional details and configuration instructions.
Ident¶
Ident is an old protocol which should no longer be used because it is insecure. It is still supported by AXS Guard for legacy reasons.
Web Access Policies¶
Web Access filters or Access Control Lists (ACL) govern the access to specific URLs and websites.
ACLs can be assigned to users, groups, computers or the entire system (a.k.a. a system-wide configuration). Group and user ACLs require authentication to be activated.
Using the Reverse Proxy for Remote Access to Terminal Servers¶
About¶
There are several methods to access a terminal server, depending on their type, e.g. Remote Desktop Gatway (RDG) servers and servers which provide web-based services (HTTP) require a different setup and approach, i.e. by using the AXS Guard reverse proxy.
Note that an Enterprise Software Bundle is required to use the AXS Guard reverse proxy solution presented in this section. Customers who don’t have this bundle can make use of a VPN connection instead.
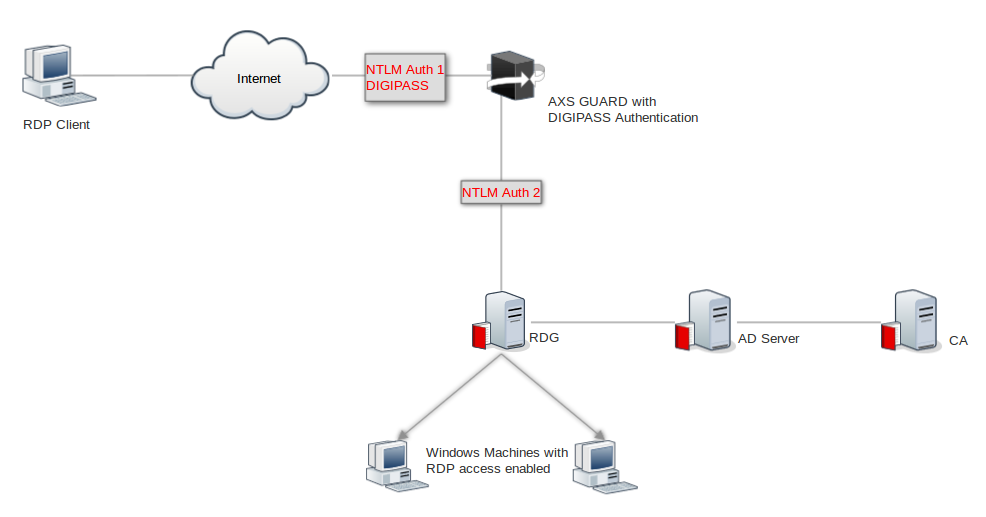
Remote Desktop Gateway (RDG)¶
This setup relies on the RDP protocol and is a secure solution to remotely access your RDG applications. 2FA authentication can be enforced by AXS Guard.
See the Reverse Proxy guide and KB section on this site for additional information and step-by-step configuration examples.
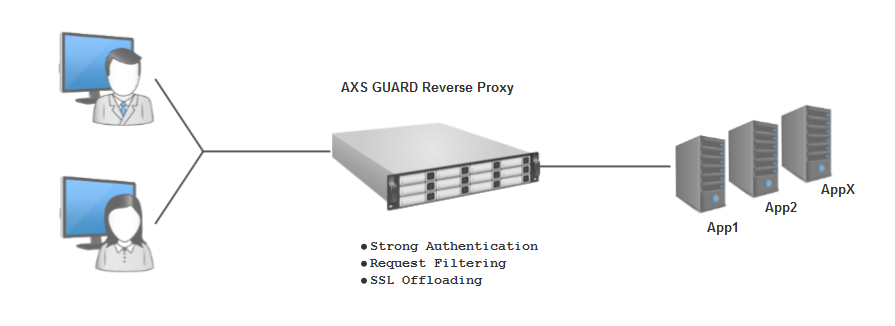
Reverse Proxy Web Services¶
For web-based services such as Awingu, Citrix and XenApp. See the Reverse Proxy manual for additional information and configuration instructions.
Access through a VPN¶
It is possible to securely access terminal servers via one of the AXS Guard VPN services, e.g. OpenVPN, SSTP or L2TP. See the relevant setup guides on this site for additional information and configuration instructions.