WireGuard S2S Configuration¶
1. Introduction¶
1.1 About¶
WireGuard is a modern, fast, and secure VPN protocol designed to be simple and efficient. Its state-of-the-art cryptography and Linux kernel integration make it an ideal choice for high-performance, site-to-site connections. This document is intended for system administrators and focuses exclusively on site-to-site VPN setups, enabling secure communications between multiple networks.
The instructions provided in this document are based on the diagram shown below, representing a basic site-to-site VPN setup. It serves as a foundational example to help you get up and running quickly. If your environment has stricter security needs or more complex requirements, be sure to review the security recommendations and adjust your configuration as needed.

1.2 Protocol Essentials¶
| Aspect | Details |
|---|---|
| Defaults | WireGuard exclusively uses the UDP protocol and 51820 is the common default listen port. If a listen port is not explicitly specified in the WireGuard tunnel interface configuration, the system will automatically select a random UDP port to listen for incoming traffic. |
| Listen Port | The port number can be changed as needed, particularly if the default port is blocked or conflicts with another service. |
| Firewall | When setting up a WireGuard server, it's crucial to ensure the firewall allows traffic on the chosen port (default or custom). |
| NAT | WireGuard can operate when one peer is behind standard NAT or CGNAT, provided the NATed peer initiates the connection. For the tunnel to persist when idle, enable the PersistentKeepalive setting on the NATed peer; this keeps the NAT mapping alive, allowing continued communication. |
2. Feature Activation¶
-
Log in to your AXS Guard appliance.
-
Go to System > Feature Activation > VPN.
-
Enable the WireGuard feature.
3. Configuration¶
3.1 Create Tunnel Interface¶
- Log in to the AXS Guard appliance (HQ).
- Navigate to VPN > WireGuard > Interfaces and click the
+button. - Enter the required information (refer to the context-sensitive help for details). Use the interface address as shown in our example:
10.0.0.0/32. - Save the configuration.
-
Repeat steps 1-4 on the remote appliance (Satellite Office), using the interface address
10.0.0.1/32as shown in our example.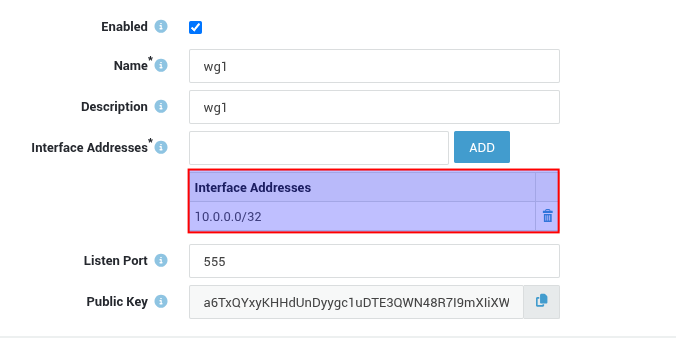
3.2 Peer Configuration¶
- Navigate to VPN > WireGuard > Peers on the HQ side.
- Click the
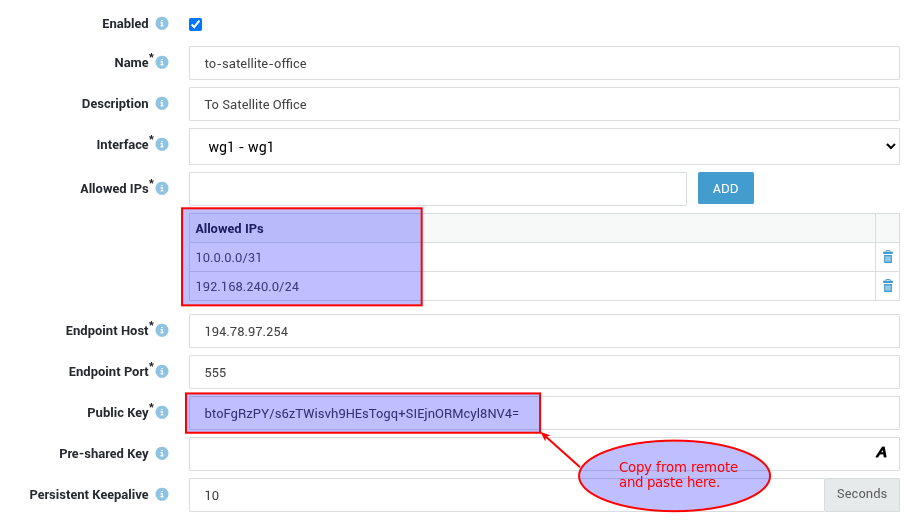
+button to configure a new peer. - Enter the required information (refer to the context-sensitive help and our example for details).
- Copy and paste the public key from the remote tunnel interface.
- Save your configuration.
-
Repeat steps 1-5 on the remote appliance (Satellite Office).
4. Firewall & Network Setup¶
4.1 Policies¶
4.1.1 WireGuard Traffic¶
You'll need to configure each endpoint to allow WireGuard traffic between the peers (see our example). We'll start with HQ. Repeat the following steps on each endpoint:
- Navigate to Firewall > Rules > Towards.
-
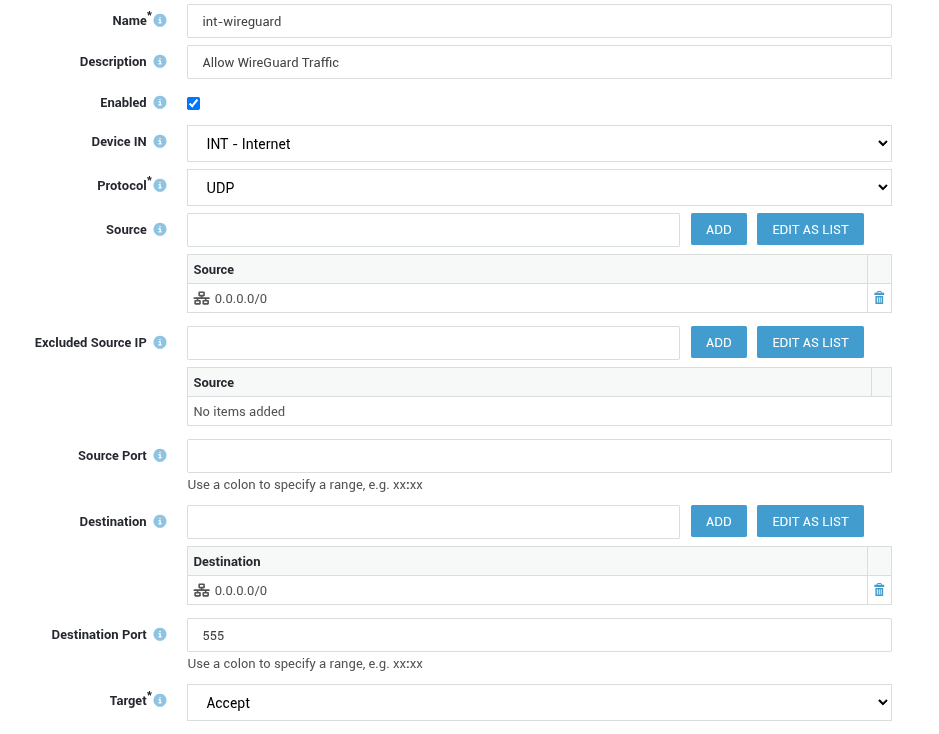
Add a new rule to allow WireGuard traffic over the Internet, as shown in the example below:
-
Navigate to Firewall > Policies > Static.
- Edit the
stat-intpolicy and add the rule created in step 2. -
Save your configuration.

-
Repeat steps 1-5 on the remote appliance (Satellite Office).
4.1.2 Tunnel Traffic¶
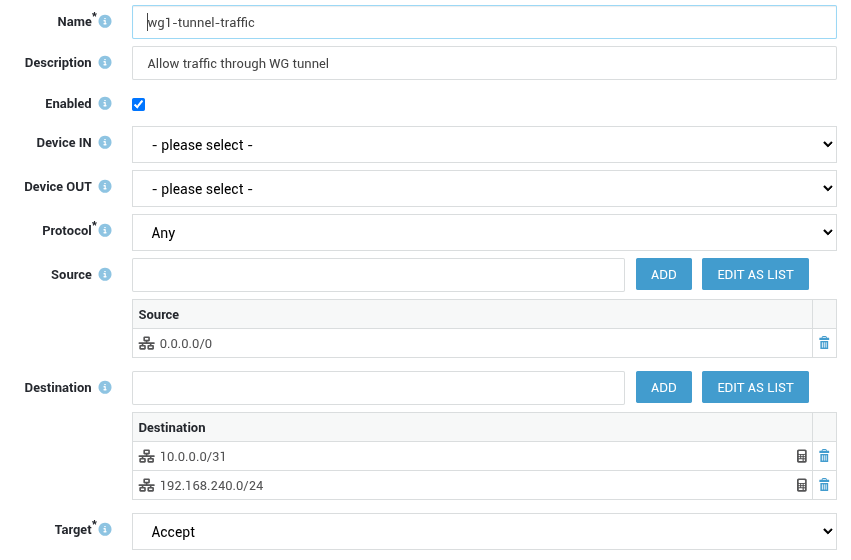
Next, you must allow traffic through the WireGuard tunnel for the allowed IPs defined in the peer configuration. We'll start with HQ. Repeat the following steps on each endpoint:
- Navigate to Firewall > Rules > Through.
-
Add a new rule as shown in the example below:
-
Navigate to Firewall > Policies > Static.
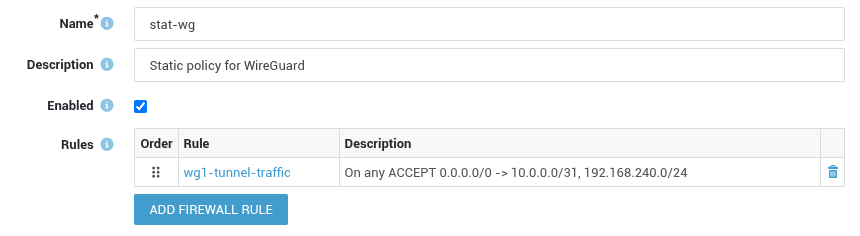
- Create a new static firewall policy for WireGuard, e.g.
stat-wg. -
Assign the rule created in step 2 and save your configuration.
-
Repeat steps 1-5 on the remote appliance for networks
10.0.0.0/31and192.168.250.0/24(Satellite Office).
4.2 Routing¶
To facilitate communication between allowed networks (IP ranges) across a WireGuard tunnel, static routing entries are essential. Each WireGuard endpoint must be configured with static routes that direct traffic intended for the peer's allowed IPs through the WireGuard tunnel interface. These routes can be configured manually or automatically. We'll start with HQ.
4.2.1 Manual Configuration¶
- Navigate to Network > Routing.
-
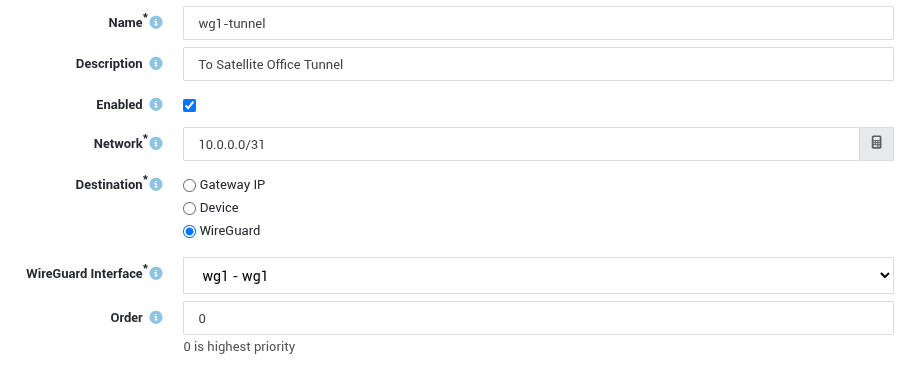
Add a new route for the WireGuard tunnel devices:
-
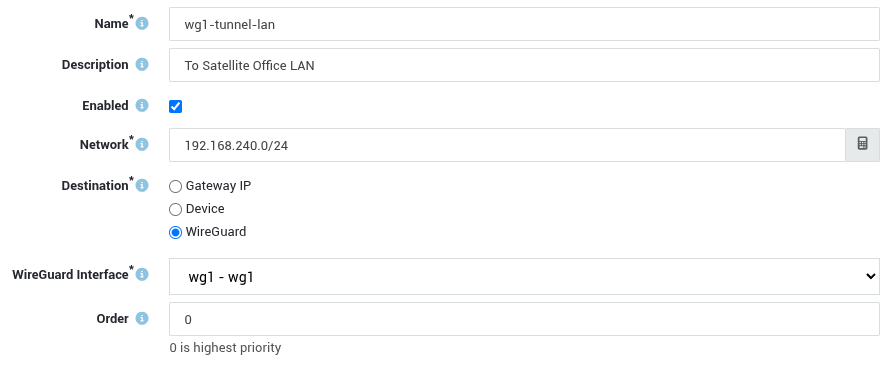
Add a new route for the peer's allowed IPs (see example).
-
Repeat steps 1-3 on the remote appliance for networks
10.0.0.0/31and192.168.250.0/24(Satellite Office).
4.2.2 Auto-configuration¶
- Navigate to WireGuard > Peers.
- Enable Generate routes and save your configuration.
-
Repeat these steps on the remote appliance.
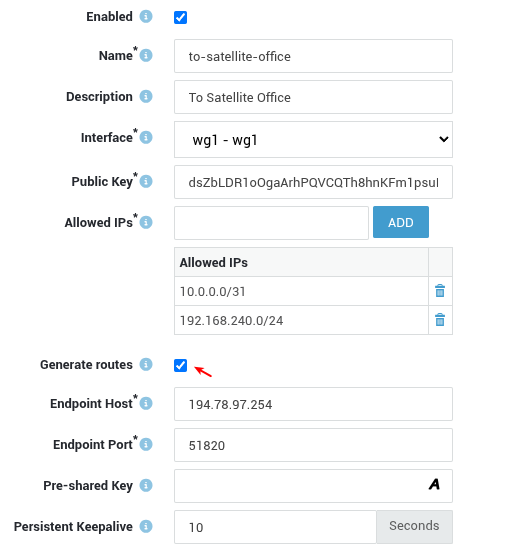
Important
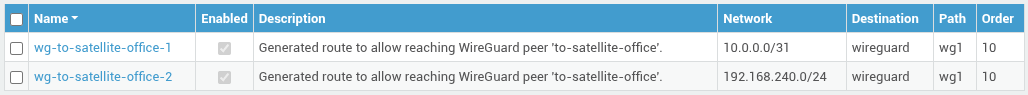
You can find the added routes under Network > Routing. Each generated route will be formatted as wg-[peer name].
5. Status & Controls¶
5.1 Peer Status¶
The status of WireGuard peers can be checked in one of two ways: either via the dashboard or via the WireGuard status menu.
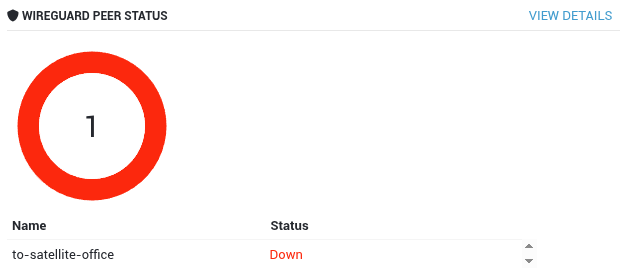
5.1.1 Dashboard¶
- Log in to your AXS Guard appliance.
-
Check the system's dashboard.
5.1.2 WireGuard Status¶
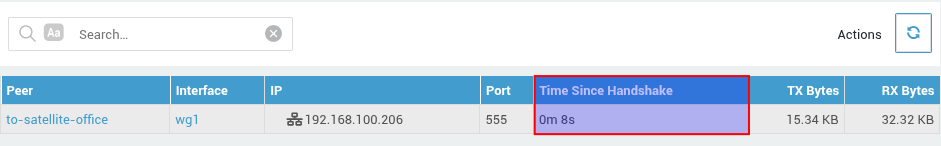
- Log in to your AXS Guard appliance.
-
Navigate to VPN > WireGuard > Status to verify the status:
5.2 Restart WireGuard¶
- Navigate to VPN > WireGuard > Peers.
-
To disable and re-enable the tunnel, toggle the Enabled flag.

5.3 Logging¶
WireGuard logs provide valuable insights into the operational status and behavior of the WireGuard tunnel interfaces. They reveal key information regarding peer connectivity, handshake processes, and keepalive mechanisms.
- Navigate to VPN > WireGuard > Logs.
- Click on the appropriate date to view the log entries.
-
Switch between raw (technical view) and parsed (formatted view) logs to find the information you need.
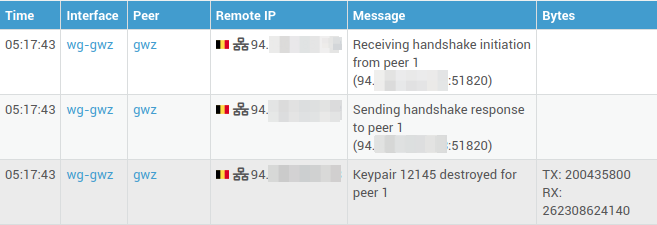
5.3.1 Parsed View¶
5.3.2 Raw View¶
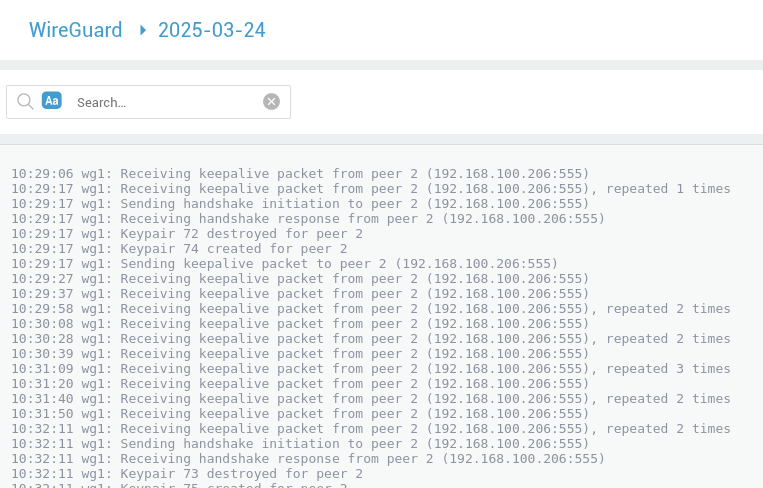
Key log entries can be categorized into several areas:
Keepalive Packets: These entries, such as Receiving keepalive packet from peer [peer_ID] ([IP_address:port]), confirm the ongoing communication between peers. These packets are essential for connection maintenance and peer liveness detection. The repeated [n] times notation indicates potential network anomalies like jitter or packet loss.
Handshake Events: Log entries indicating Sending handshake initiation to peer [peer_ID] and Receiving handshake response from peer [peer_ID] detail the periodic cryptographic key renegotiation. Keypair [keypair_ID] destroyed for peer [peer_ID] and Keypair [keypair_ID] created for peer [peer_ID] logs confirm the successful key rotation, which is vital for tunnel security.
Peer State Changes: Log messages like Peer [peer_ID] destroyed and Peer [peer_ID] created reflect changes in the configured peers. These entries document the removal and addition of peers, respectively.
6. Security Recommendations¶
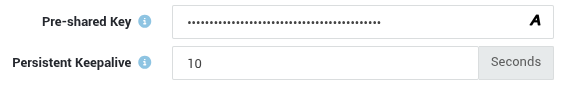
6.1 Pre-Shared Keys¶
Adding a Pre-Shared Key (PSK) provides an extra layer of cryptographic security by combining symmetric-key encryption with the existing public-key-based key exchange. System administrators should use a unique PSK per tunnel for maximum security.
The PSK should be 256 bits (32 bytes) in length and Base64-encoded.
You can generate a 256-bit PSK using standard Linux tools like openssl, e.g.
$ openssl rand -base64 32
6.2 Firewall Rules¶
Implement strict firewall rules to control traffic passing through the WireGuard interface. Specify source and destination addresses, allowed protocols, and ports. As WireGuard permits bidirectional communication by default, it's essential to define rules that explicitly manage network traffic direction to prevent unintended access.
6.3 Allowed IPs¶
Carefully configure the Allowed IPs setting in your WireGuard configuration. Only allow the necessary IP ranges to pass through the tunnel. This principle of least privilege is very important.
6.4 Updates¶
Maintain up-to-date WireGuard software and operating systems to patch any known security vulnerabilities.
7. Support¶
7.1 If you encounter a problem¶
If you encounter a problem with AXS Guard, follow the steps below:
-
Check the troubleshooting section of the feature-specific manual.
-
Check the knowledge base on this site for information about special configurations.
-
If no solution is available in any of the above sources, contact your AXS Guard vendor.
7.2 Contact Information¶
(+32) 15-504-400
support@axsguard.com