Wireshark over SSH¶
About this Document¶
In this document, we explain how to run Wireshark on your desktop (Linux or Windows) and capture traffic on a remote AXS Guard appliance via a secure connection.
Before you start¶
See the CLI guide, which explains how to install the necessary tools to remotely access the AXS Guard console. You will need:
-
An AXS Guard user with CLI privileges
-
Linux: ssh and ssh-keygen
-
Windows: PuTTY, PuTTYgen and plink
Using PuTTY and Wireshark¶
PuTTY¶
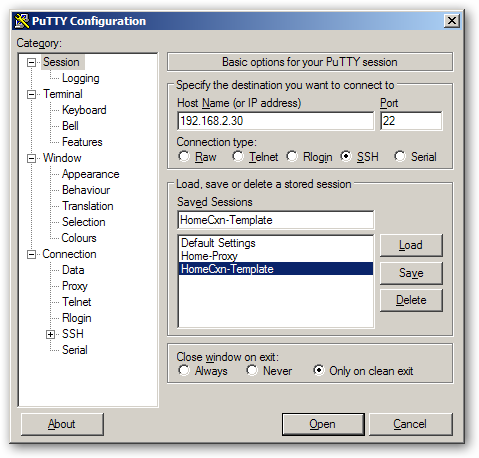
Make sure to save a session in PuTTY as shown in the example below. This will simplify the command line input. Store the following data in your saved session:
-
The AXS Guard IP address (Session → Host Name (or IP address) )
-
The AXS Guard username (Connection → Data → Auto-login username)
-
The user’s private key file (Connection → SSH → Auth → Private key file for authentication)
Wireshark¶
-
Download and install Wireshark on your PC.
-
Use Wireshark over SSH.
Linux¶
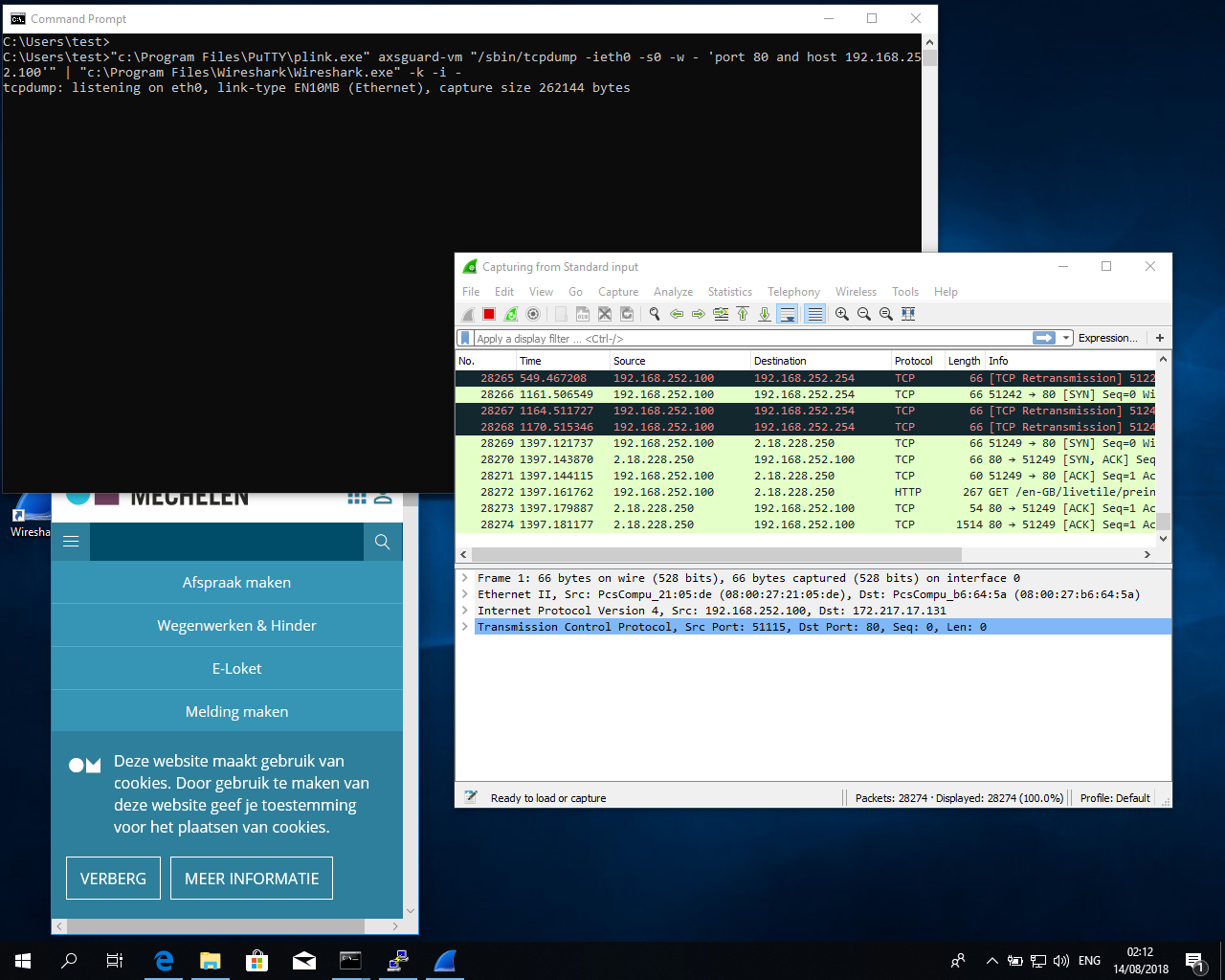
ssh -i [/path/to/your/private key] [your user]@[AXSGuard IP] "tcpdump -ieth0 -s0 -w - 'port 3128 and host 192.168.1.5'" | wireshark -k -i -
The above command will run tcpdump on AXS Guard and capture full packages (-s0) from eth0 for a certain host and destination port. The output is sent over SSH to your desktop PC’s "stdout" where Wireshark is waiting on "stdin" for input. (-k means start immediately). You can modify the tcpdump filter settings. Make sure you filter as much as possible on the AXS Guard side; a remote capture session can become quite heavy on the network, depending on the application and filter specifications.
Windows¶
In Windows, we will make use of plink, a command-line connection tool similar to UNIX ssh. Open a command prompt and execute the following commands (change the paths according to your file locations):
“C:\Program Files\PuTTY\plink.exe” -batch -i [/path/to/your/private key.ppk] [your user]@[AXSGuard IP] "tcpdump -ieth0 -s0 -w - 'port 3128 and host 192.168.1.5'" | “C:\Program Files\Wireshark\Wireshark.exe” -k -i -
If you saved a PuTTY session with the correct private key, username and IP address, you can use the short version as shown below.
“C:\Program Files\PuTTY\plink.exe” -batch [my-saved-session] "tcpdump -ieth0 -s0 -w - 'port 3128 and host 192.168.1.5'" | “C:\Program Files\Wireshark\Wireshark.exe” -k -i -
The aforementioned commands will run tcpdump on AXS Guard and capture full packages (-s0) from eth0 for a certain host and destination port. The output is sent over SSH to your desktop PC’s "stdout" where Wireshark is waiting on "stdin" for input. (-k means start immediately). You can modify the tcpdump filter settings. Make sure you filter as much as possible on the AXS Guard side; a remote capture session can become quite heavy on the network, depending on the application and filter specifications.
The result will look something like this: