Never Trust, Always Verify¶
Zero Trust Network Access (ZTNA) is an evolving strategy, not a one-time purchase or solution. AXS Guard provides the tools and expertise to establish the groundwork for a customized zero-trust framework that suits your business needs.

Understanding ZTNA¶
Zero Trust Network Access (ZTNA) is a security framework that establishes an identity- and context-aware perimeter around applications and network resources, ensuring they remain invisible to unauthorized users. It verifies not only who you are, but also the context of your access, such as location, time, and compliance with security policies, before access is granted.
Essentially, ZTNA solutions have two core functions:
- Enforcing Zero Trust Principles: Ensure that access to applications and network resources is strictly based on verified identity and context, preventing unauthorized lateral movement within the network.
- Facilitating Secure Network Access: Provide the necessary means for authenticated users to securely access authorized applications and network resources.
While all ZTNA solutions aim to achieve these goals, they differ in the specific technologies they offer. These technological choices can give certain products an advantage or make them more suitable for particular business cases.
Unlocking ZTNA with AXS Guard¶
AXS Guard delivers the core capabilities of Zero Trust Network Access (ZTNA) by decoupling policy enforcement from basic network connectivity. With this separation, gaining access to the network does not imply access to all applications and network resources, nor does it reveal which applications exist on the network.
OpenVPN: ZTNA in Action¶
In this use case, AXS Guard leverages the OpenVPN tunneling protocol as the secure on-ramp to your network, but access controls don't stop at the tunnel. Once a connection attempt is made, Zero Trust kicks in immediately. AXS Guard performs strict authentication checks:
Validation of geographic location using GeoIP data.
Verification of a valid client certificate.
Assessment of the client version.
Extra authentication of the user, for example through two-factor authentication (2FA) or an identity provider.
Devices that fail any of these checks are denied access outright. This approach also drastically reduces the attack surface. Once a secure tunnel is established, identity- and feature-based access policies take control. These policies:
Dynamically create logical access boundaries around individual network
resources.
Enforce protocol- and port-specific firewall policies.
Prevent lateral movement based on who the user is and what they're allowed to do.
Unlike static firewall rules, these access controls adapt in real time
to user roles and contextual conditions, ensuring that users only reach
what they're explicitly authorized to access.
Bottom line: Network access doesn't equal access to network resources or
applications. With our ZTNA approach, every session is governed by Zero
Trust.
Why OpenVPN?¶
AXS Guard champions the OpenVPN protocol for remote network access because it provides a highly robust and flexible ZTNA solution. This effectiveness largely stems from OpenVPN's IP-layer connectivity, which ensures native support for all internet application protocols, both current and future.
Other solutions that don't operate at the IP layer often limit you to a narrow set of applications, typically web-based ones. They frequently attempt to convert popular protocols like RDP and SSH into HTTPS, which can lead to limitations and complications. OpenVPN, by contrast, offers full network access, guaranteeing compatibility for all your IP-based applications without compromise.
Here are some additional key reasons why AXS Guard leverages the OpenVPN protocol:
- OpenVPN is continuously enhanced, a prime example being the recent Data Channel Offload (DCO) improvements. This innovation significantly boosts data throughput by offloading data channel processing to the AXS Guard kernel, achieving speeds close to line rate.
- The OpenVPN protocol is inherently firewall-friendly, which is crucial for users connecting from diverse Wi-Fi and other access networks. Furthermore, AXS Guard has built-in mechanisms to prevent Denial-of-Service (DoS) and brute-force attacks, ensuring your network resources remain consistently available.
- Unlike many ZTNA solutions that assume client-initiated traffic, OpenVPN tunnels facilitate network-level access, allowing application servers to initiate communication with devices. This is vital for scenarios like device management, where an application server might need to push software patches or erase data on a target device. This bidirectional capability is often missing in ZTNA solutions which aren't based on network tunneling.
- OpenVPN stands out as a *proven and secure *choice. As an open-source technology, it offers full transparency and has undergone extensive, independent security audits. This contrasts sharply with proprietary ZTNA solutions and closed network tunneling protocols.
- OpenVPN tunnels, combined with mutual authentication based on certificates, provide a unique digital identity for IoT devices. This enables least-privilege access even for unattended, always-on IoT connections. Many ZTNA solutions not built on network tunneling protocols often overlook the specific security requirements of IoT devices, leaving a significant gap in an organization's security posture.
- The AXS Guard OpenVPN Access Server is designed to integrate seamlessly into your ZTNA strategy. Featuring strong user authentication and precise access control, it greatly simplifies the deployment of secure remote access within your organization.
The ZTNA Client Advantage¶
Our OpenVPN implementation specifically requires an OpenVPN client for remote access. These clients are widely supported across all major mobile and desktop operating systems. At AXS Guard, we believe a client-based approach offers the most secure and comprehensive solution compared to web-based alternatives. Here's why:
- Security is our top priority. Clientless access, such as browser-based access, often lacks mutual authentication, as browsers typically don't require a certificate to access web servers. This significantly broadens the attack surface. With OpenVPN, the use of valid certificates is always required, ensuring only legitimate and verified users can establish a connection.
- Universal application compatibility. Not all applications are browser-based. Many critical business tools, such as the Remote Desktop Protocol (RDP), require dedicated client software to function. Our client-based approach ensures full compatibility with these applications.
- Secure mobile access. The landscape of business applications is rapidly shifting towards private mobile applications, developed for internal company use, as organizations move away from relying on browser-based access for critical mobile workflows. Our client-based solution provides the secure access these private mobile apps require, a capability largely unattainable with browser-only solutions.
- Identity-based firewalling. AXS Guard is designed to enforce identity-based security, where firewall policies are dynamically applied based on the authenticated user or device. These policies govern network access for users depending on their authentication status and assigned network privileges.
Monitoring & Threat Protection¶
Even after a user successfully authenticates and gains access, the vigilance doesn't end. Instead, it transitions into a crucial phase of continuous monitoring. This ongoing oversight of user activity and network traffic is paramount because traditional, perimeter-based security models are no longer sufficient against sophisticated threats.
By continuously analyzing behavior patterns, deviations from normal activity, and network anomalies, organizations can swiftly detect and respond to suspicious actions that might indicate a breach, malware infection, or unauthorized data access, thereby safeguarding critical assets and maintaining the integrity of their systems.
Observe & Protect¶
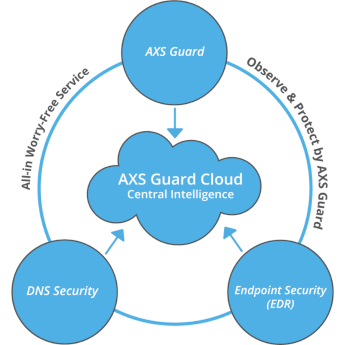
AXS Guard's Observe & Protect is a comprehensive, managed XDR (Extended Detection and Response) solution that blends cutting-edge technology with round-the-clock expert oversight.
At its core, the solution relies on a zero-trust architecture, continuously validating every user and device, and integrates multiple layers of defense. These include:
- Next-Gen Firewall & Security Platform: safeguards your network borders with intrusion prevention, content filtering, web security, and DNS threat protection.
- Endpoint Security (EDR): leverages AI to detect and respond to advanced threats across all endpoints.
- Threat Intelligence Premium Pack: boosts defenses using GeoIP filtering, DNS security, plus advanced scanning of web and email content.
- AXS Guard Cloud: centralizes management and real-time threat intelligence in a cloud-based portal.
SOC Monitoring¶
All components are backed by 24/7 SOC monitoring, including health checks, installation, incident response, and scheduled reporting. The service is compliance-friendly, supporting frameworks like GDPR, HIPAA, ISO 27001, and NIS 2, and is scalable to adapt as your user base grows.
Conclusion¶
AXS Guard ZTNA redefines secure access, putting both robust protection and effortless user experience at the forefront. By adopting a never trust, always verify approach, it drastically enhances your security posture, ensuring that only authenticated users gain access to specific applications and defined network resources -- not your entire network.
This granular control significantly reduces the attack surface and thwarts lateral movement of threats.
AXS Guard solutions are incredibly user-friendly. Their intuitive design and transparent operation mean users can seamlessly access the resources they need, when they need them, fostering productivity without compromising on the unwavering security demanded by today's dynamic digital landscape.